2018 Archive
- ⬅ All articles
- 🗂 Categories
- 🔖 ftp (1)
- 🔖 infrastructure (3)
- 🔖 privacy (1)
- 🔖 compliance (1)
- 🔖 client-side (1)
- 🔖 general (84)
- 🔖 blog (6)
- 🔖 press (2)
- 🔖 australia (1)
- 🔖 client (17)
- 🔖 release (81)
- 🔖 article (14)
- 🔖 security (24)
- 🔖 server (19)
- 🗄 Archive
- 📌 2001 (3)
- 📌 2005 (1)
- 📌 2006 (1)
- 📌 2007 (1)
- 📌 2008 (1)
- 📌 2012 (1)
- 📌 2013 (3)
- 📌 2014 (13)
- 📌 2015 (20)
- 📌 2016 (23)
- 📌 2017 (14)
- 📌 2018 (38)
- 📌 2019 (17)
SFTPPlus Release 3.43.0
Wed 19 December 2018 | general release
We are announcing the latest release of SFTPPlus version 3.43.0.
New Features
- When defining a new password for an account, it is now possible to define a minimum level of complexity and strength. [#4700]
- You can now set an email as part of the user's account details. [#5125]
- You can now allow FTP/FTPS users to change their passwords. [server-side][ftp][ftps] [#5127]
- The bundled OpenSSL library was updated to OpenSSL 1.1.0j on Windows, SLES 11, and OS X. [#5148]
- A new event handler was added for extracting GZIP compressed files to a destination folder. [#5150]
- Debian 8 (Jessie) on X86_64 is now a supported operating system. [#5152]
Defect Fixes
- SFTP and SCP file transfer services no long fail when the client is sending a "keep alive" global request. [server-side][sftp][scp] [#5149]
- We have updated the libraries used by SFTPPlus with patches addressing CVE-2013-7459 and CVE-2018-6594.
Deprecations and Removals
- Debian 7 is no longer supported as it was replaced by Debian 8. [#5152-1]
- Solaris 11 on SPARC and X86 is no longer receiving new SFTPPlus updates due to weak demand for Solaris 11 and increasing costs in keeping Solaris 11 infrastructure up to date. [#5152]
You can check the full release notes here.
Pro:Atria and SFTPPlus sponsor DVLA Code Challenge 2018 for School Children
Tue 18 December 2018 | article general
Pro:Atria is delighted to be a sponsor of the DVLA Code Challenge 2018 for School Children.
DVLA runs the competition to provide Schools, Code Clubs and Community groups in Wales with IT equipment and promote STEM (Science, Technology, Engineering and Mathematics) subjects aimed at children aged 7-14.
DVLA work with a number of Volunteer Organisations and Charities such as STEM Learning and Code Club (part of the Raspberry Pi Foundation Charity) to help teach children aged 7-14 Information Technology subjects in Primary Schools. This initiative is focused on a competition is to get children involved with coding games while providing an incentive and opportunity for the Schools and Clubs to win IT equipment and to promote the work of the volunteers and Charity organisations that actively engage with and support the schools to run these clubs.
The children choose from a number of themes provided by the associates and write a game to enter. Prizes are awarded to the teams reaching the final and every school or group that enters the competition or attends the event, either at the venue or via a live link is entered into a prize draw. The prize draw element encourages greater participation in schools so that we can reach as many schools and groups as possible - there are about 2200 in Wales.
In 2017 the project was able to place IT Equipment in over 50 Schools and groups in Wales and get hundreds of children aged 7 – 11 involved in coding.
In 2018 the event was even more successful with over 60 Primary and Secondary Schools across Wales winning prizes in the DVLA Code Challenge Competition.
Mark Jones, Head of Cyber Security Testing at DVLA said:
"All the entries we had this year were of a very high quality which shows just how much talent is out there, we just need to provide opportunities for the children to use it. This year we had 258 Entries from Primary Schools and 58 entries from Comprehensive Schools."
He went on to say:
"250 children aged 7 – 14 and teachers attended the event in the Richard Ley Development centre and a further 170 individuals from had stands and exhibits outside the venue. We could have filled the venue more than twice with the requests for tickets. We ran a Live Link and between 3000 and 4000 people watched the event stream with over 2500 votes cast for the winning entries."
This year there were 8 finalists and 1 special prize Finalists prizes in 7 – 11 category and 11 – 14 category.
The winners were:
7 – 11 Age Group
1st Prize - £2000 - BlaenBaglan Primary
2nd Prize - £1500 - Usk CiW Primary School
3rd Prize - £1000 - Gwyrosydd Primary School
Runner Up - £750 - Cadle Primary School
11 - 14 Age Group
1st Prize - £2000 - Cathedral School
2nd Prize - £1500 - Caerleon Comprehensive School
3rd Prize - £1000 - Dyffryn Conwy
Runner Up - £750 - Cyfarthfa High School
Special Prize Pontlliw Primary School
Beach Ball Bingo Winners 23 Schools won Lego Boost Educational Kits, Sparx Spheros and OhBot robotic heads.
Prize Draw Winners A further 28 Schools winning similar prizes
Tim Adams, Director of Pro:Atria said:
"We were delighted to be involved with this worthwhile event that was hugely successful with encouraging and engaging with young people. These young people will be the future coders and vital to the economic success of the country for decades to come. Our congratulations to all the winners as well as all entrants for their participation.To have so many enthusiastic children thinking and learning about all aspects of computers, gaming and security while winning IT equipment for the schools is a huge win/win for everyone involved and the DVLA is to be congratulated on organising such a successful event. We look forward to being part of the 2019 Challenge and hope that even more schools will be involved."
Further information from:
http://dvlacodechallenge.dvla.gov.uk/
About Pro:Atria Ltd:
Our worldwide customer profile includes government agencies and businesses large and small across Europe, USA, Middle East, Asia, Australia and Far East. Pro:Atria also works with integrators and system design teams including IBM, DXC, Fujitsu, Capita and Tata (amongst others). Customers are from all sectors including retail, financial, manufacturing, healthcare, education and transport as well as government agencies and departments. Support is provided by our team of staff who are based across Europe.
About SFTPPlus:
SFTPPlus MFT is a software suite for managed file transfer (MFT) with Client and Server that may be licensed and used as standalone modules or together as a MFT solution. SFTPPlus MFT provides functionality to automate file transfers between systems, users inside an organization and with third-parties. The software is designed to work on major operating systems including Windows, Linux and UNIX. SFTPPlus MFT supports the most popular file transfer protocols like FTPS, SFTP, HTTPS and WebDAV and provides external authentication support, integration with built-in and external logging solutions and audit functionality. SFTPPlus MFT also integrates with external encryption solutions and offers an API for third-party integrations.
Secure your FTPS server with Let's Encrypt
Thu 29 November 2018 | article
Introduction
What is Let's Encrypt?
Let's Encrypt (sometimes shortened as LetsEncrypt) is a certificate authority that provides SSL/X.509 certificates at no charge. You can read more on the subject in the Wikipedia article on Let's Encrypt.
A Let's Encrypt certificate is valid for 90 days, but it is recommended to renew it 30 days before expiration.
Certificates are provided using an automated process designed to automate creation, signing, installation, and renewal of certificates for websites in a secure manner.
Only Domain-validated certificates are being issued. Organization-Validated and Extended Validation (EV) Certificates are not available.
How does Let's Encrypt work?
Let's Encrypt uses the Automatic Certificate Management Environment (ACME) protocol.
ACME is a communications protocol for automating interactions between certificate authorities and their users, allowing automated deployments of public key infrastructure (PKI).
SFTPPlus as an ACME client
SFTPPlus implements the client side of the ACME protocol.
It can connect to the Let's Encrypt ACME server, and automatically request SSL/X.509 certificates, free of cost.
To prove that it has administrative rights over a domain, SFTPPlus runs an embedded HTTP server, available over port 80, which implements the HTTP-01 challenge of the ACME protocol.
SFTPPlus can automatically request certificates for HTTPS and FTPS file transfer services, as well as for the Local Manager web console.
The obtained certificates are signed by the Let's Encrypt authority, which is automatically trusted by all modern operating systems. For example, an FTP client using the Windows Certificate Store will automatically accept the certificate used to encrypt a connection to a SFTPPlus server using Let's Encrypt.
All this is done automatically through SFTPPlus' seamless Let's Encrypt integration. You only need to configure the domain name, SFTPPlus will take care of the rest. No need to use external tools like letencrypt.exe, store or copy files in directories like /etc/letsencryt or C:siteswwwroot.
Let's Encrypt and FTPS
While Let's Encrypt was created for HTTPS websites, you can use the same certificate signed by Let's Encrypt's Certificate Authority for FTPS communication.
You can use Let's Encrypt for any secure FTP protocol, be it Explicit FTPS or Implicit FTPS. The certificates can be used over both SSL and TLS, including TLS 1.2.
You still need to have port 80 opened or forwarded to SFTPPlus for the automated certificate generation and renewal.
Check our dedicated documentation page to see how to enable Let's Encrypt for your FTPS server.
This resource is written as of SFTPPlus version 3.42.0.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Release 3.42.0
Tue 27 November 2018 | general release
We are announcing the latest release of SFTPPlus version 3.42.0.
New Features
- You can now define a custom CSS file for HTTP/HTTPS file transfer services. [server-side][http][https] [#5101]
- You can now automatically get SSL/X.509 certificates signed by Let's Encrypt's certificate authority. [ftps][https] [#5117]
- The sample init scripts were updated to allow starting SFTPPlus directly under an unprivileged service account. [#5132]
- It is now possible to set a database event handler which will automatically delete older events. In this way you can limit the size of the database. [#5137]
- Amazon Linux 2 on X86_64 is now a supported platform. [#5139]
Defect Fixes
- The MySQL database resource is no longer erroneously marked as requiring a restart in the Local Manager. [#5137]
You can check the full release notes here.
SFTPPlus Release 3.41.1
Wed 21 November 2018 | general release
We are announcing the release of SFTPPlus version 3.41.1 which is a bugfix release to always transfer the marker file as the last file in marker based batch transfer.
By transferring the marker file as the last file, a failed transfer can be resumed.
No other changes were done in this release on top of 3.41.0.
Defect Fixes
- In marker based batch transfer, the marker file is now always transferred last. [client-side] [#5143]
You can check the full release notes here.
SFTPPlus Release 3.41.0
Thu 15 November 2018 | general release
We are announcing the release of SFTPPlus version 3.41.0 which adds support for running HTTP/HTTPS services behind a Layer 7 HTTP Application load balancer.
New Features
- It is now possible to define a list of HTTP Host header origins accepted by the HTTP file transfer services and the Local Manager. This allows running compatible SFTPPlus services behind a load balancer without compromising on the default CSRF checks. [server-side][http][https] [#5138]
You can check the full release notes here.
SFTPPlus Release 3.40.1
Wed 14 November 2018 | general release
We are announcing the release of SFTPPlus version 3.40.1 which is a bugfix release. Starting with this version, the option to hide the SFTPPlus authentication session from the www-authenticate headers is visible in the Local Manager.
No other changes were done on this release on top of 3.40.0
Defect Fixes
- The option to hide the SFTPPlus authentication session from the www-authenticate headers is now visible in the Local Manager. [server-side][http][https] [#5134]
You can check the full release notes here.
SFTPPlus Release 3.40.0
Tue 13 November 2018 | general release
We are announcing the latest release of SFTPPlus version 3.40.0.
New Features
- SuSE Enterprise Linux without the Security Module and OS X are now distributed with OpenSSL 1.1.0h, making it possible to use TLS 1.2 and SHA2. [#5030]
- It is now possible to use variable placeholders when defining the path for the local file event handler. [#5095]
- You can now define the SSH keys used by the SFTP/SCP file transfer service and by the SFTP location as text values inside the configuration file. Storing SSH keys in external files is still supported. [sftp][scp] [#5096]
- You can now define the SSL certificate and key pairs used by HTTPS/FTPS and the local manager services as text values inside the configuration file. [ftps][https] [#5097]
- You can now hide the SFTPPlus session authentication method from the www-authenticate header. This can be used as a workaround for an authentication issue when using SFTPPlus with older HTTP clients, which don't recognize multiple www-authenticate headers. [server-side][http][https] [#5099]
- It is now possible to make the files of an account available over HTTP as a public file transfer site. No username or password is required to access and manage those files. [server-side][http][https] [#5100]
- It is now possible to filter event handlers based on the source IP address. [#5120]
Defect Fixes
- When an SFTP transfer (upload or download) is interrupted, a dedicated event is emitted. In previous versions, no event was emitted to signal the transfer failure. [server-side][sftp] [#5027-1]
- When an SCP transfer (upload or download) is interrupted, the emitted events now clearly signal the transfer failure. In previous versions, the same events as for a successful transfer were emitted. [server-side][scp] [#5027]
- SFTPPlus no longer uses the MIME type database provided by the operating system. In older operating systems like SuSE 11, the MIME type for JavaScript files was defined as text/x-js, which caused failures in modern versions of Chrome and Firefox. SFTPPlus now defines the MIME type as application/javascript on any operating system. [local-manager] [#5075]
- The speed for listing the folder content using the FTP/FTPS or HTTP/HTTPS file transfer services was improved. The improvement is observed especially on Windows, and when listing folders hosted by a remote Windows or NFS share. [server-side][ftp][http] [#5083]
- The SCP server will now use the correct name to write a file when the client is requesting an upload without providing the base path. In previous versions, a file named '-t' was created instead. [server-side][scp] [#5094]
Deprecations and Removals
- Event with ID 20107 was removed and replaced with the event with ID 20158. [#5095]
- Events with ID 30013, 30048, 30052 were removed and replaced with the generic event ID 20077. Event with ID 30075 was removed and replaced with the generic event with ID 20158. [server-side][sftp][scp] [#5096]
- Loading of SSL/X.509 certificates and keys from .DER files was removed. You should convert your certificates and keys to PEM format. PEM format is the only format supported by SFTPPlus. DER support was removed, as not all of its features were supported. For example, loading the certificate chain or using multiple certificate authorities was only supported for the PEM format. [ftps][https] [#5097-1]
- Loading the certificate authority configuration from a directory containing multiple files is no longer supported. You can still use multiple certificate authorities for the same configuration by storing all the CA certificates in the same file. [https][ftps] [#5097]
You can check the full release notes here.
SFTPPlus Release 3.39.0
Fri 05 October 2018 | release security
We are announcing the latest release of SFTPPlus version 3.39.0.
Customers using the SCP protocol are urged to upgrade to this version. Any previous version contains a security issue when overwriting files over SCP.
New Features
- In the event handler configuration, it is now possible to filter the events based on their groups. [#2483]
- When the remote FTP/FTPS server supports the MLST command, SFTPPlus will use it to determine the existence of remote paths. [client-side][ftp][ftps] [#3885]
- The events emitted at the start or at the end of a client-side file transfer now contain the size of the file, duration and transfer speed. [client-side] [#5067]
Defect Fixes
- When overwriting files using the SCP file transfer, the content of the existing file is completely erased. In previous versions, when overwriting an existing file with a new file which was smaller in size, the resulting file would still have the file size of the previous file, with the extra data kept from the previous file. [security][server-side][scp] [#5087]
- When using execute_on_destination_before in a transfer for which the destination location is stopped, the transfer will automatically start the location. In previous versions, the transfer would failed as the location was stopped, requiring a manual start of the location. [client-side] [#3511]
- When checking the existence of a remote FTP file, the operation now fails when the server returns an error other than 'Path not found'. In previous versions, the error was ignored and the path was considered as non-existing. [client-side][ftp][ftps] [#3576]
- FTP/FTPS client operation can now successfully detect the absence of a file on a remote server. [client-side][ftp][ftps] [#3885]
- You can now disable the timeout for the FTP data connection by setting its value to 0. In previous versions, when set to 0, the connection was disconnected right away due to the timeout. [server-side][ftp][ftps] [#5049]
- When changing the extra_data configuration for the HTTP event handler, the Local Manager UI now shows that a restart is required for the event handler. [#5079]
- You can now change from the Local Manager the list of SSH ciphers available to the SFTP and SCP file transfer services. This was a regression introduced in 3.37.0. [server-side][sftp][scp] [#5085]
Deprecations and Removals
- When a FTP server-side operation fails due to a permission error, the error code is now 553. In previous versions, it was 550, which was the same error code for Path not found or the generic error code for other error cases. [server-side][ftp] [#3576]
You can check the full release notes here.
SFTPPlus Release 3.38.0
Fri 21 September 2018 | general release
We are pleased to announce the latest release of SFTPPlus version 3.38.0.
New Features
- When the remote FTP/FTPS server supports the MLST command, SFTPPlus will use it to determine the existence of remote paths. [client-side][ftp][ftps] [#3885]
- For a transfer, it is now possible to execute on destination commands which will include the source and destination path and file name. [client-side] [#4522]
- New permissions allow-create-folder, allow-delete-folder, allow-delete-file, and allow-set-attributes were added to help defining a stricter configuration. [server-side] [#4955-1]
- A new permission, deny-full-control was added to deny any action to the configured path. [server-side] [#4955]
- You can now add custom values to the JSON payload sent by the HTTP event handler. This allows sending SFTPPlus HTTP events to existing webhooks like Slack or Splunk. [api] [#5068]
Defect Fixes
- FTP/FTPS client operation can now successfully detect the absence of a file on a remote server. [client-side][ftp][ftps] [#3885]
You can check the full release notes here.
SFTPPlus Release 3.37.1
Thu 13 September 2018 | security release
We are pleased to announce the latest release of SFTPPlus version 3.37.1.
Defect Fixes
- The HTTP API authentication for an account now fails when the account is accepted by the remote HTTP API but the associated group is disabled. [server-side][security] [#5058]
- A defect was fixed in Local Manager which was causing the Local Manager to fail on Internet Explorer 11. [#5061]
Deprecations and Removals
- Event with ID 20060 was removed and replaced by event with ID 20136. [server-side] [#5058]
You can check the full release notes here.
SFTPPlus Release 3.37.0
Thu 06 September 2018 | general release
We are pleased to announce the latest release of SFTPPlus version 3.37.0.
New Features
- The HTTP and HTTPS file transfer API now support session based authentication. The Basic Auth login is still supported. [server-side][http][https] [#5009-1]
- The HTTP and HTTPS file transfer services now have a session based login page. The Basic Auth login is still supported for web clients which don't support cookies. [server-side][http][https] [#5009]
- LDAP authentication method was extended to allow defining a LDAP filter for LDAP users which are allowed to act as administrators through the Local Manager service. [manager] [#5010-1]
- You can now define multiple authentication methods for the Local Manager service. [manager] [#5010-2]
- OS authentication method was extended to allow defining a list of Operating System account groups which are allowed to act as administrators through the Local Manager service. [manager] [#5010]
- You can now use Local Manager to configure the accounts and groups of the local-file authentication method. [#5041]
- It is now possible to configure an event handler filter based on excluded usernames or components by using the ! (exclamation mark) to mark a value which needs to be excluded. [server-side][client-side] [#5043]
- The MDTM FTP command now shows microseconds when displaying time. [server-side][ftp][ftps] [#93-1]
- The FTP/FTPS server now supports MLST and MLSD commands (Listings for Machine Processing) as specified in RFC 3659. [server-side][ftp][ftps] [#93]
Defect Fixes
- The authentication process now fails when an authentication is configured but not running. In previous versions, the stopped authentication method was skipped, and the authentication process continued with the next configured method. [security] [#5010]
- When sending files to an FTP or FTPS destination location, transfers will no longer saturate the network, instead they will follow the TCP congestion signaling. In previous versions this issue was causing excessive memory usage and transfer failures over low bandwidth networks. [client-side][ftp][ftps] [#5033]
- Comma-separated values in Local Manager can now be configured using a simple free-text input box. This allows editing existing values and makes it easier to reorder them. [management] [#5043]
Deprecations and Removals
- HTTP file transfer service API now uses cookie-based authentication by default. In previous versions the default authentication method was HTTP Basic authentication, which remains an available method. [server-side][http][https][#5009-1]
- The HTTP file transfer service API now uses JSON as the default content type for responses. In previous versions you would have to explicitly ask for JSON. Now, you need to explicitly ask for HTML. [server-side][http][https] [#5009]
- Events with ID 20005 and 50008 were removed and replaced with event 20136. Events with ID 20135 and 20138 were removed and replaced with event 20142. [#5010-1]
- Event with ID 50009 was removed, as OS administrators now use the OS authentication method. [#5010-2]
- With the introduction of multiple authentication methods for the Local Manager service, you will now need to explicitly define the [server] manager_authentications configuration option. If manager_authentications is not defined (or left empty), SFTPPlus will fall back to the first defined Application authentication method. [#5010-3]
- The include_os_group configuration options for roles was removed. Now you can explicitly define an OS authentication method for the Local Manager server. include_os_group was replaced by the manager_allowed_groups configuration option for the OS authentication method. [server-side] [#5010]
You can check the full release notes here.
SFTPPlus Release 3.36.0
Thu 02 August 2018 | general release
We are pleased to announce the latest release of SFTPPlus version 3.36.0.
New Features
- The Azure File Service of the Azure Storage Account is now available as a location for client-side transfers. [client-side][http] [#4988]
- It is now possible to define a client-side file transfer that will wait for a signaling filename before it starts transferring the files. [client-side] [#4989]
- It is now possible to configure transfers which will monitor the source recursively and will then transfer to the same non-recursive destination. [client-side] [#4998]
- It is now possible to configure a transfer rule which will use a destination file name that is different to the source name. [client-side] [#5007]
Defect Fixes
- The Windows installer is now signed. [#4794]
- It is now possible to clear the data attributes and structured fields configuration for an event handler and the allowed groups for an OS authentication mode from the Local Manager. In previous versions saving these configuration changes was generating an error. [#5018]
- When the local file event handler is rotating the files based on time, it now preserves the file extension. In previous versions the timestamp was used as the file extension. [#5036]
You can check the full release notes here.
Secure File Transfer and Business Continuity Planning
Fri 06 July 2018 | article
Introduction
What is business continuity planning (BCP)?
According to Wikipedia, business continuity planning is the process of creating systems of prevention and recovery to deal with potential threats to a company.
Business Continuity Planning also includes these five components as defined by the SANS Institute. These components are:
- Business Resumption Plan
- Occupant Emergency Plan
- Continuity of Operations Plan
- Incident Management Plan
- Disaster Recovery Plan (DRP)
We have decided to provide a high level overview for this article. While secure file transfer is just a component of business continuity planning, it is still an important component of it. We hope that after reading this post, that you also recognize secure file transfers to be part of the Business Continuity Planning process.
Assigning risk ratings
Planning involves conducting a risk assessment of your organization. In this case, planning involves determining what is considered IT risk versus Business risk.
By conducting a risk analysis, you can identify portions of your business resources, identify known risks to these business resources, and assign a risk rating.
According to the Cisco Systems Network Security Policy Best Practices White Paper, the following are rating guidelines based on a three-tier risk level. These are examples from purely a network security level and there are other models and guidelines available that cover a more generalized approach.
The following are excerpts from the above whitepaper:
Low Risk
These are systems or data that if compromised (data viewed by unauthorized personnel, data corrupted, or data lost) would not disrupt the business or cause legal or financial ramifications. The targeted system or data can be easily restored and does not permit further access of other systems.
Medium Risk
These are systems or data that if compromised (data viewed by unauthorized personnel, data corrupted, or data lost) would cause a moderate disruption in the business, minor legal or financial ramifications, or provide further access to other systems. The targeted system or data requires a moderate effort to restore or the restoration process is disruptive to the system.
High Risk
These are systems or data that if compromised (data viewed by unauthorized personnel, data corrupted, or data lost) would cause an extreme disruption in the business, cause major legal or financial ramifications, or threaten the health and safety of a person. The targeted system or data requires significant effort to restore or the restoration process is disruptive to the business or other systems.
From the perspective of secure file transfer, you will need to consider at which level your assets (such as the assets covered in the scope of file transfers) fall under which of these risk categories.
Establishing a business continuity structure / policy
Part of the planning process also involves establishing a business continuity structure.
Having a business continuity policy will require building a team and a governance structure around it. Within the policy, ensure to outline the roles and responsibilities of those that are going to be impacted by this document.
Within the context of secure file transfers, the policy could outline the role of the secure file transfer administrator and to make aware that it is their responsibility to ensure successful Continuity of Operations. In this example, the same administrator could also be the support or testing lead to ensure that the failover file transfer system is tested and verified should there be an issue with the main server.
On that note, for those interested in more details about how SFTPPlus can help administrators meet Continuity of Operations demands, please read our introduction to SFTPPlus and high availability or resiliency environments.
In conclusion, the business continuity policy should ensure that the organization has been provided a general understanding of the policy, purpose, guidelines and definitions around the business continuity plan.
Incident Management and Incident Response
Part of business continuity planning is around incident management and incident response.
What is the relationship between Business Continuity Planning and Incident Management Plan? According to NIST Security Incident Handling guide (the National Institute of Standards and Technology), “organizations should ensure that incident response policies and procedures and business continuity processes are in sync. Computer security incidents undermine the business resilience of an organization. Business continuity planning professionals should be made aware of incidents and their impacts so they can fine-tune business impact assessments, risk assessments, and continuity of operations plans.”
Within the context of secure file transfers, SFTPPlus emits an audit trail for administrators to monitor events and for audit assurance purposes, which can help assist in incident management and response. For further readings about procedures, we recommend the NIST Security Incident Handling guide. Our documentation on the audit trail also provides a useful starting point on how you can administer SFTPPlus to be compliant to your auditing needs.
Implementation
Implementation is the practice stage. The importance of implementation is the prevention of business risk.
The recovery point objective (RPO) and recovery time objective (RTO) are baseline data that administrators should be aware of when implementing the business continuity plan.
For example, a secure file transfer administrator can ask themselves questions such as "What is the recovery time actual (RTA) in contrast to the recovery time objective (RTO) for the file transfer application during an actual disaster or exercise?"
The Business Impact Analysis should uncover which systems are mission critical and non-critical, which can further impact the RPO and RTO, as an example. In this example, you may need to ensure an active-active high availability setup is in place with the backup server in the cloud rather than on-premise. In this scenario, you may be targeting 100% Recovery Consistency Objective (RCO) for a business process.
Exercise / Testing / Action
Part of business continuity plan should include a review process to modify the existing policy. This process should be able to adapt to lessons learned - either from an actual disaster event or from an exercise.
The review process ensures that the policy, posture and practices are being re-evaluated accordingly.
The Business Continuity Plan should end up being a dynamic document that can adapt to the constantly changing business and IT environment and needs. This dynamic should also include education and evaluation of staff skills involved.
ISO guidelines for further reading
Continual improvement with your business continuity plan are also covered by guidelines such as ISO 22301 "Societal security -- Business continuity management systems --- Requirements". This guide “specifies requirements to plan, establish, implement, operate, monitor, review, maintain and continually improve a documented management system to protect against, reduce the likelihood of occurrence, prepare for, respond to, and recover from disruptive incidents when they arise.”
And for those focusing on the information security management system, the ISO/IEC 27001:2013 standard “specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system within the context of the organization. It also includes requirements for the assessment and treatment of information security risks tailored to the needs of the organization.”
This resource is written as of SFTPPlus version 3.34.1.
The details in this resource is for guidance only. Influences such as own security policies, requirements, and threat models should be considered when adopting this type of guidance.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Release 3.35.0
Tue 03 July 2018 | security release
We are pleased to announce the latest release of SFTPPlus version 3.35.0.
New Features
- The OpenSSL library used by SFTPPlus on Windows was updated to OpenSSL 1.1.0h. [#4579]
- It is now possible to define virtual folders that are available to all accounts from a group. These virtual folders can point to directories outside an account's locked home folder. [server-side] [#4928]
- It is now possible to allow authentication of operating-system accounts only for those belonging to a configured group. [server-side] [#4962]
- Python version on all supported platforms except HP-UX was updated to 2.7.15. Consequently, the Expat libraries bundled with Python were updated to 2.2.4 on these platforms. [#4579]
Defect Fixes
- An internal error is no longer raised when a SSH client sends a message for a method which is not supported by the SSH transport. Instead, the client receives a standard SSH not-implemented error. [server-side][sftp] [#4579]
- The speed of the SSH handshake for the SFTP service has been improved. Previously, there was a noticeable difference for certain customers during the SSH handshake authentication process. [server-side][sftp][#4579]
- pyOpenSSL was updated on AIX and Solaris to fix CVE-2013-4314. The X509Extension in pyOpenSSL before 0.13.1 does not properly handle a '0' character in a domain name in the Subject Alternative Name field of an X.509 certificate, which allows man-in-the-middle attackers to spoof arbitrary SSL servers via a crafted cert issued by a legitimate Certification Authority. The experimental packages for HP-UX are still vulnerable to this and will to be fixed in a future release.[server-side][#4579]
- Once set, passwords for locations or email resources are no longer readable from Local Manager. A password can be read only before being set and applied. Afterwards, its value cannot be read, only updated. [security] [#4938]
- Comma-separated configuration values may now contain comma characters, as long as they are enclosed in double quotation marks. [#4951]
- The event generated when a peer's certificate validation fails during a TLS/SSL handshake now shows the detailed error message, not just the error code. [#4979]
You can check the full release notes here.
Setting up security scanners for your SFTPPlus MFT Server
Wed 20 June 2018 | article security
Introduction
The following is a short guide on how you can set up a security scanner for your SFTPPlus MFT Server installation. For this guide, we have chosen a free and open source scanner, OWASP Zed Attack Proxy or zaproxy, as an example.
Of course, there are a number of other software and tools that you can use and all with varying mileage.
We can also cover these other tools, depending on interest. Therefore, if you would like to see more of these types of posts from SFTPPlus, please make sure to contact us. If you are not familiar with the terms, or need to do some background reading, you can scroll down to the Other resources section first.
To be kept up to date with the latest developments, please sign up to our security advisories.
About OWASP Zed Attack Proxy or zaproxy
For our server-side scan of the SFTPPlus MFT service (HTTPS and HTTP) and Local Manager, we used the OWASP Zed Attack Proxy or zaproxy which is a free and open source penetration testing tool released by OWASP and developed for website application security testing.
After running the application, you can generate a report for further consumption. The report contains OWASP ZAP specific terminology. These are listed below for your reference.
WASC ID This is the ID provisioned by the Web Application Security Consortium (WASC) Threat Classification project. Read more about WASC here.
CWE ID This is the ID provisioned by the Common Weakness Enumeration (CWE) project. Read more about CWE here.
Confidence This is the description of how confident the result is in the validity of the finding.
- False Positive - for potential issues that one will later find is actually not exploitable.
- Low - for unconfirmed issues.
- Medium - for issues that zaproxy is somewhat confident in.
- High - for findings that zaproxy is highly confident in.
- Confirmed - for confirmed issues.
Risk Description of how serious the risk is. The risk shown is from the report generated by zaproxy.
Source This is the ZAP policies code. Read more here.
Using zaproxy to conduct an active scan on SFTPPlus services
Prerequisite
As a standard prerequisite, you will need the zaproxy application, a version of SFTPPlus Server software and consent to conduct these types of scanning activities if you are doing so on behalf of a group or organization.
For this example, we will be conducting an active scan of the SFTPPlus HTTP service available on the default port 10080. There are also other web-browser based services that you can scan such as the SFTPPlus Local Manager on port 10020 and the HTTPS service available on the default port 10443.
In addition, scanning can affect availability. We recommend a backup of your database.
What is an active scan?
Active scanning will attempt to find potential vulnerabilities by using known attacks against the selected target, in this case the SFTPPlus HTTP service. It should be noted that active scanning can only find certain types of vulnerabilities. Logical vulnerabilities, such as broken access control, will not be found by any active or automated vulnerability scanning. Manual penetration testing should always be performed in addition to active scanning to find all types of vulnerabilities.
Also, scanning will unearth results that also need to be consumed and understood by the relevant parties.
Setting up an active scan
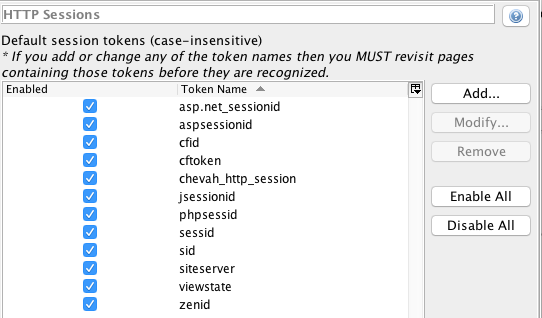
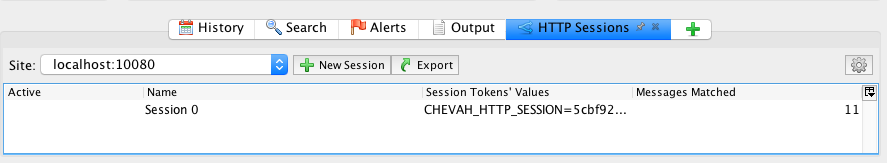
In order to attack the authenticated part of the HTTP service, we will need to add the HTTP session token in the zaproxy application.
Go to 'Tools' -> 'Options' -> 'HTTP Sessions' -> add chevah_http_session in the Token Name. Make sure that this token is enabled then select 'OK'.
See screenshot below:
Make sure that the 'HTTP Sessions' tab is open. To view the 'HTTP Sessions' tab, go to 'View' -> select 'Show Tab' -> then 'HTTP Sessions'. At this stage, the pane is empty but it will soon be populated with the correct values in the later steps.
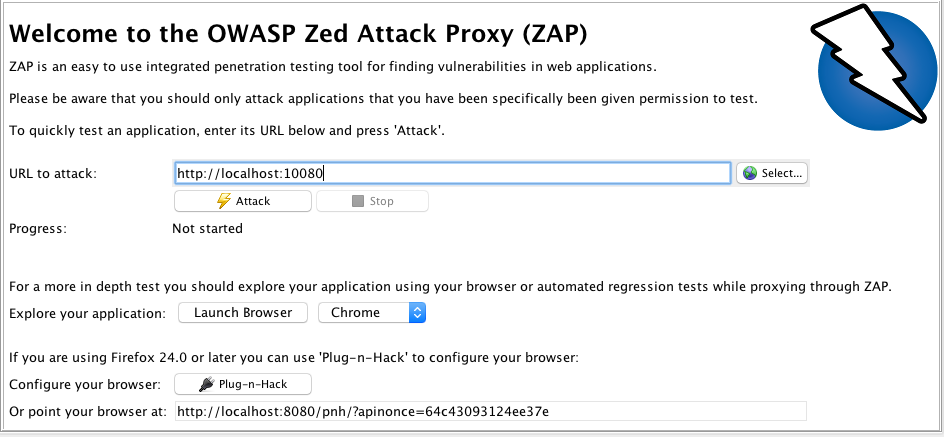
In the 'Quick Start' pane, add http://localhost:10080 in the 'URL to attack' field. This is the URL for the SFTPPlus HTTP web-browser based file manager service. Do not press 'Attack', instead scroll down and select 'Launch Browser' for Chrome.
See screenshot below:
The reason why you cannot go straight to attacking/scanning the resource is because it still requires authentication. If not authenticated with zaproxy, you will see an error Failed to attack the URL: received a 401 response code.
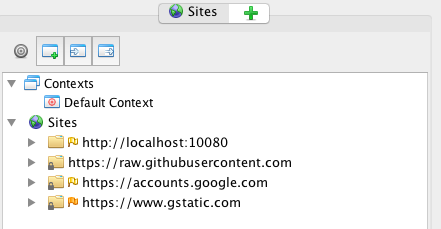
After selecting 'Launch Browser', a new Chrome browser will launch and you will start seeing activity in the 'Sites' pane. The browser should have 'Explore your application with ZAP' as the landing page.
Open the URL http://localhost:10080 in the Chrome browser and login to the test file transfer account.
Once logged in, you should now see http://localhost:10080 in the 'Sites' pane.
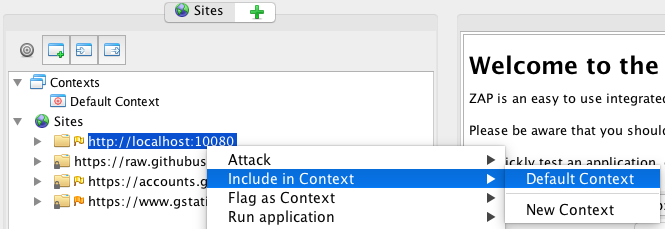
In the 'Sites' pane, right-click over the http://localhost:10080 URL and select 'Include in Context' then 'Default Context'.
In the 'HTTP Sessions' pane, you should now see that there is a new session added for the site localhost:10080 with values populated in the 'Session Tokens' Values' field.
If you do not see any values, launch the SFTPPlus HTTP service again and log in.
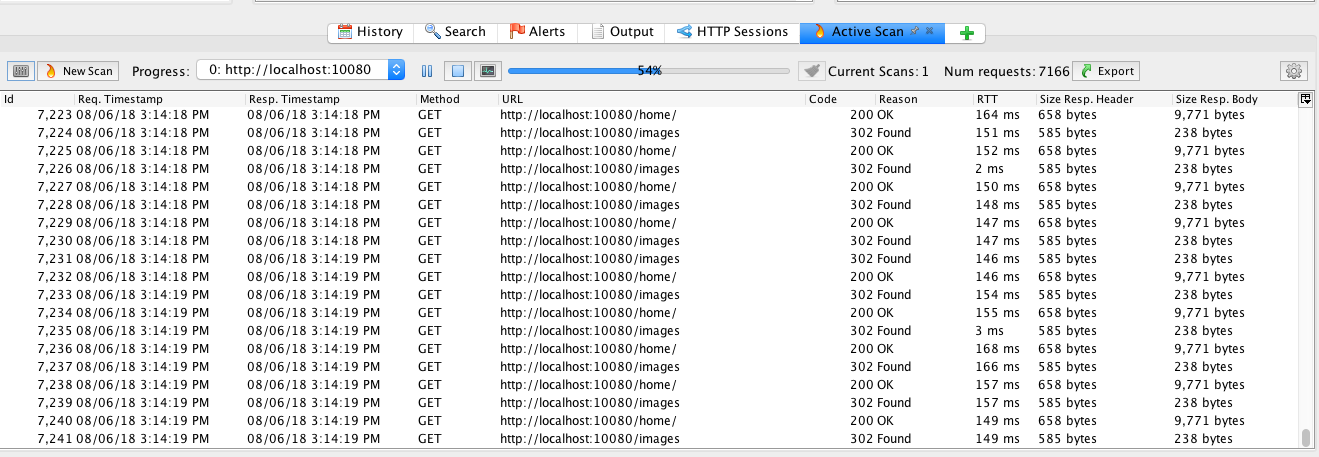
Back in the 'Sites' pane, right click over the localhost URL, select 'Attack' -> 'Active Scan'.
For one of our tests, we only wanted to scan the HTTP headers to see if the version of SFTPPlus would be able to escape possible CSRF attacks. In this case, for the 'Input Vectors' tab, only the 'HTTP Headers, All Requests' vector was selected. You can choose other vectors according to your own requirements or you can opt to choose all vectors.
Allow the scan to work. The times can vary.
Alerts are located in the 'Alerts' tab. You can read what the Alert is about from this pane. Please note that alerts may include alerts from associated third party services.
You can generate the report after the scan has completed.
Select 'Report' on the top menu > 'Generate HTML Report' and save the file.
Other reporting file formats can be used such as JSON, XML, Markdown.
Example scan result
Below is an example scan of what you may find. Please note that results will differ depending on factors such as your installation, configuration and SFTPPlus version:
Low Risk: Web Browser XSS Protection Not Enabled Details: URL: Risk: Low Confidence: Medium CWE ID: 933 - Security Misconfiguration - https://cwe.mitre.org/data/definitions/933.html WASC ID: 14 - Server Misconfiguration http://projects.webappsec.org/w/page/13246959/Server%20Misconfiguration Source: Passive (10016 - Web Browser XSS Protection Not Enabled) Description: Web Browser XSS Protection is not enabled, or is disabled by the configuration of the 'X-XSS-Protection' HTTP response header on the web server Other info: The X-XSS-Protection HTTP response header allows the web server to enable or disable the web browser's XSS protection mechanism. The following values would attempt to enable it: X-XSS-Protection: 1; mode=block X-XSS-Protection: 1; report=http://www.example.com/xss The following values would disable it: X-XSS-Protection: 0 The X-XSS-Protection HTTP response header is currently supported on Internet Explorer, Chrome and Safari (WebKit). Note that this alert is only raised if the response body could potentially contain an XSS payload (with a text-based content type, with a non-zero length). Solution: Ensure that the web browser's XSS filter is enabled, by setting the X-XSS-Protection HTTP response header to '1'. Reference: https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet https://blog.veracode.com/2014/03/guidelines-for-setting-security-headers/
Upon seeing reports in regards to XSS vulnerabilities, we have fixed user input escaping where error messages where done without the user input and also added validation of the user input.
Therefore, the HTML rendering code for the HTTP service has been added to ensure that this is not the case to secure user input.
As part of this change, we have also added new automated tests for the HTTP service as part of our quality assurance reviews.
Example SFTPPlus audit log during a scan
As you can see, the scan generated some potential CSRF attacks which SFTPPlus version 3.34.1 detected and therefore disconnected against:
| 40018 2018-06-07 11:05:43 Process Unknown 127.0.0.1:58871 Forcing client disconnection at "/unwanted.js" after receiving 0 bytes in body. Response: 400 Possible CSRF
The above is just an example of what you may see in the audit log and is not related to the scan result in the previous section.
The reason why you are seeing this in the audit trail is that we now enforce requests from the same origin including basic requests such as GET and even older HTTP requests such as POST.
This is to ensure that requests from the outside boundary (the Internet) are not interacting with the safe confines of the HTTP file service or the Local Manager.
We have ensured that the browser is forced to download data, rather than execute data, after checking the Origin and Referrer headers are of the same source.
What to do if you find an issue
The first step is to check if you have the latest version of SFTPPlus. New versions will contain not only new features, but also defect fixes including security bug fixes.
The second step is to look at the type of alert and to do a manual confirmation of the feasibility of the alert (for example, if it's a false positive) and to confirm the results from zaproxy. The alerts are meant to be guidance for further investigations.
If there is a bug found, please do not hesitate to contact SFTPPlus Support with your defect report.
Keep up to date by signing up to our security advisories
SFTPPlus continues to be focused on automated, non-interactive file transfers in a secure fashion. Our security practices have been designed to make this a reality for our clients.
To be kept up to date with the latest security advisory and news, please subscribe to out newsletter here.
Other resources
The details in this resource is for guidance only. Influences such as own security policies, requirements, and threat models should be considered when adopting this type of guidance.
This resource is written as of SFTPPlus version 3.34.1.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Release 3.34.1
Fri 08 June 2018 | security release
We have recently deployed the latest release of SFTPPlus version 3.34.1 which fixes the following defects:
- The files downloaded using the HTTP file transfer service now have explicit headers to disable caching. [security][http][https] [#4953]
- The HTTP service no longer returns user input as part of the error messages. [security][http][https][server-side] [#4954]
You can check the full release notes here.
IPv6 support for HTTP/S, FTP/S, SFTP and SCP File Transfer Services
Mon 04 June 2018 | article infrastructure
Why get ready for IPv6?
According to the Akamai Q1 2017 State of the Internet Connectivity Report, "approximately 5 million IPv4 addresses were depleted from available pools at the Regional Internet Registries in the first quarter, leaving approximately 39 million addresses remaining."
In response to the steady depletion of IPv4 addresses, we see greater adoption of many large mobile and broadband networks actively rolling out IPv6 connectivity. According to World IPv6 Launch, among the top 10 participating networks with more than half IPv6 deployment rates include Comcast, ATT, Verizon Wireless and Deutsche Telekom AG.
Now is a good time to brush up on your knowledge of deploying IPv6 in your organization. For those with a lack of knowledge or training in IPv6 implementation, there is an even greater urgency when addressing the potential security impact of the rollout in the organization. Such scenarios are amplified when administrators do not have the required level if minimal expertise in IPv6 to ensure there is protection against threats. If you are in the front-line of IPv6 deployment and file transfers in your own organization, you will find this post of useful interest.
A brief introduction to IPv6
IPv6 was first introduced by IETF in 1998, via RFC 2460, which has since been updated via RFC 8200 published in July 2017. This is the new version of the Internet Protocol and a successor to IPv4.
The main updates are as follows:
Expanded addressing capabilities
This involves increasing the IP address size from 32 bits to 128 bits. This allows greater support in addressing hierarchy, more addressable notes, scalability of multicasting, and addition of anycast address.
Simplified header formats
This involved dropping or making optional some of the IPv4 header fields.
Improved support for extensions and options
The way IP header options are encoded allows for more efficient forwarding and greater flexibility for new options.
Flow labeling capability
This allows sender requests to be treated in the network as a single flow.
Authentication and privacy capabilities
Extensions are added in order to support authentication, data integrity, data confidentiality.
While it has been some length of time since the first introduction, each day brings forward the pressing need to implement IPv6 as IPv4 addresses become exhausted. Greater adoption for IPv6 by vendors, including increase in knowledge and support, means that deployment is now more feasible for administrators than ever before.
IPv6 and SFTPPlus
Enabling IPv6 on SFTPPlus for HTTP/S, FTP/S, SFTP and SCP
SFTPPlus supports configuring IPv6 addresses for the HTTP, HTTPS, FTPS, FTP, SFTP and SCP file transfer services.
We have written a starter guide with details on how you can enable IPv6 with SFTPPlus. Please to go to the documentation section on IPv6 support.
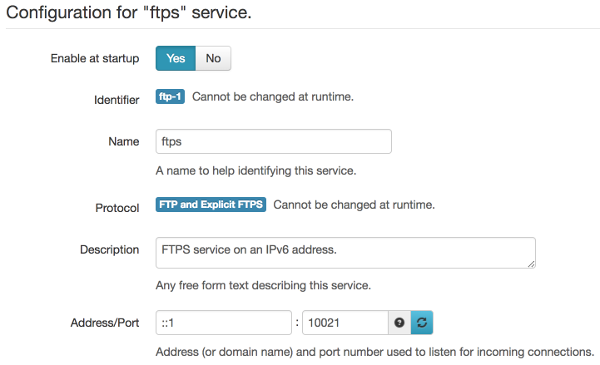
When configuring a new service on SFTPPlus, an IPv6 address can be used. To accept connections on all available IPv6 interfaces, simply use the :: address like the simplified test configuration below:
[services/ftps] enabled: Yes name: FTPS Service on an IPv6 address. address: ::1 port: 10021
Please consult the configuration documentation for more details about each type of file transfer service.
Enabling IPv6 on SFTPPlus Local Manager
Similar to enabling IPv6 on file transfer services, you can set the SFTPPlus Local Manager to listen in on an IPv6 address via the same address field as the services.
Administrators can add this via the SFTPPlus Local Manager Services section:
Enabling authentication methods with IPv6
We support IPv6 address when authentication file transfer accounts via the ldap authentication method and via the HTTP API authentication method.
IPv6 implementation and security considerations
The following are some considerations in implementing IPv6 securely.
Conduct an inventory audit
Tag which file transfer scenarios (server, client, protocol) require IPv6 implementation and support.
Communicate with your vendors
Notify your vendors as to what level of support is provided for IPv6. If not supported, inquire if there will be plans on the product roadmap for the support.
We have added IPv6 support for file transfer services, as of SFTPPlus version 3.33.0, in response to customer needs to roll out such support.
Conduct a security-focused audit on IPv6 deployment
Both IPv4 and IPv6 share similar properties when it comes to security. In this case, take an audit of which of these properties can be carried over within an IPv6 deployment.
Last but not least - do not overlook security risks and requirements for IPv6
Network administrators overlooking the effects of IPv6 in their network will face security risks. IPv6 packets is susceptible to attacks like MITM (Man-in-the-Middle) attacks. Bad actors may also attempt to eavesdrop by making use of upper-layer protocols such as TLS (Transport Layer Security) or SSH (Secure Shell). Another potential security threat is bypassing IPv4-only firewalls and ACLs using functional IPv6 tunneling protocols as described in the Carnegie Mellon University CERT/CC blog post here.
IPv6 troubleshooting
The following are introductory advice for those troubleshooting IPv6 within a file transfer scenario.
- Ensure that the protocols to be used are fully tested with SFTPPlus.
- Ensure that FTP proxies, firewalls and other layer 7 technologies properly support IPv6.
- Ensure that any other boundary facing technologies are implementing IPv6 correctly.
It is also good to keep note of future changes to the protocol. For example, design changes to the new IPv6 extension header could mean security implications based on how the new changes work with existing extension headers.
Those evaluating SFTPPlus and customers with a valid support contract can leverage help from the SFTPPlus Support team for queries in regards to SFTPPlus and IPv6 deployment.
Other resources
- World IPv6 Launch
- SANS Institute InfoSec Reading Room guide on IPv6 Attack and Defense
- IETF specification on IPv6 on RFC 8200
- List of IPv6 RFCs and Standards Working Groups
- Infosec Today on basic IPv6 Security Considerations
- Internet Society IPv6 Case Studies
This resource is written as of SFTPPlus version 3.34.0.
The details in this resource is for guidance only. Influences such as own security policies, requirements, and threat models should be considered when adopting this type of guidance.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Release 3.34.0
Mon 28 May 2018 | security release
We are pleased to announce the latest release of SFTPPlus version 3.34.0.
A number of changes have been made in regards to how permissions are set in SFTPPlus.
If you are planning to upgrade your existing installation and you have custom permissions for SFTPPlus accounts and / or groups, we encourage you to read the changes below as it may affect your configuration.
New Features
- You can now set up an UNC path or a symbolic link to Windows Shares as home folder for an account. [#4635]
- The HTTP/HTTPS file transfer service and the Local Manager service now provide the option to configure a set of headers which are sent for all responses. You can use this to set the Strict-Transport-Security header or the use a custom Server header in an attempt to conceal the identity of the server. [security] [#4784]
- The LDAP authentication method can now connect to LDAP servers using IPv6 address literals. [server-side] [#4824-1]
- It is now possible to dynamically associate LDAP accounts to SFTPPlus groups based on arbitrary LDAP entry attributes. This is designed to augment the LDAP configuration without requiring any updates to the LDAP database. [server-side] [#4824]
- We now provide limited support for running SFTPPlus on legacy Windows 2003 Servers. For more details, check the known issues section in our documentation. [#4896]
- Ubuntu 18.04 LTS on X86_64 is now a supported platform. [#4912]
- A new permission, allow-traverse, was added to allow viewing only the folder structure without any files. In this way, accounts can traverse the folder hierarchy without seeing what files are already there. [#4931]
- A new permission allow-list was added to allow configuration of only the folder/directory listing operations. This has no effect for the SCP protocol, as the protocol itself does not support the folder listing operation. [#4932]
- A new permission allow-rename was added to allow configuration of only the rename operations available in the SFTP and FTP/FTPS file transfer servers. [#4933]
- The Ban IP for a time interval authentication method is now enabled by default in new installations. [#4934]
Defect Fixes
- The HTTP/HTTPS file transfer service and the Local Manager service now advertise a set of HTTP headers to mitigate CSRF and XSS attacks. [security] [#4930]
- The low-level JSON-RPC used by the Local Manager service now explicitly informs the web browser not to cache its POST responses. In the previous version, only GET requests were instructing the web browser not to cache the response. [security] [#4937]
- The LDAP authentication method no longer accepts credentials with empty passwords. [server-side][security] [#4939-1]
- When receiving a request which is authenticated via SSH key or SSL/X.509 certificates, the LDAP authentication method now emits a message informing that only password credentials are supported. [server-side] [#4939]
Deprecations and Removals
- The allow-read permission will no longer allow listing the content of a folder. If you want to allow folder listing, you will need to update the configuration and add the new explicit allow-list permission. [#4932-1]
- The error message returned when denying a folder listing operation was changed to include allow-list instead of the previous allow-read details. [#4932]
- The error message returned when denying a rename operation was changed to include allow-rename instead of the previous allow-full-control details. [#4933]
You can check the full release notes here.
Secure cipher suites for the ssl_cipher_list configuration
Thu 03 May 2018 | security
Default SSL cipher suites
With the release of SFTPPlus 3.32.0, we have changed the default set of SSL cipher suites for the Local Manager and the HTTPS service. As with any product that runs in many environments, SFTPPlus uses a default set of SSL-related parameters that are a compromise between security and compatibility. Up to SFTPPlus version 3.31.0, we were using this highly compatible, but still reasonably secure, default set:
ssl_cipher_list = 'ALL:!RC4:!DES:!3DES:!MD5:!EXP'
Starting with SFTPPlus version 3.32.0, we strongly emphasize our focus on security. The default setting for OpenSSL cipher suites in SFTPPlus is now:
ssl_cipher_list = 'HIGH:!PSK:!RSP:!eNULL:!aNULL:!RC4:!MD5:!DES:!3DES:!aDH:!kDH:!DSS'
Notice that we now derive our default set from the HIGH set of cipher suites in OpenSSL. As improved cipher suites are added in OpenSSL, and new vulnerabilities are discovered and patched for, this specific set of cipher suites will be continuously improved upon by the OpenSSL developers. By keeping OpenSSL libraries updated through OS-specific procedures, our customers' SFTPPlus installations will benefit from these upstream improvements.
This new default set of safe cipher suites is also encapsulated within the secure configuration option, so you may simply use the following:
ssl_cipher_list = secure
Testing your HTTPS server
In ensuring that the secure configuration option for ssl_cipher_list in SFTPPlus is actually secure enough for your needs, you should try auditing your HTTPS setup using the Qualys SSL Labs' SSL Server Test.
This is a free online service that performs an analysis of the configuration of any public HTTPS server listening on the standard 443 port. When results are submitted, a grade from A to F is provided. You can read more about Qualys' SSL Server Rating Guide in their GitHub wiki here.
Assuming you are using a modern version of OpenSSL, such as version 1.0.2, a default installation of SFTPPlus version 3.32.0 will currently yield a score of B. This is because we still care about compatibility with older clients in the default setup.
However, you might want to go beyond that and try to obtain a Qualys SSL Server Rating of A for your SFTPPlus installation. A set of ciphers suites that sacrifices a bit of compatibility to reach the Grade A rating would be:
| ECDHE-RSA-AES128-SHA:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES128-GCM-SHA256: | ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-GCM-SHA384
Keep in mind that clients such as Internet Explorer on Windows XP, Java 6.x clients and Android 2.x users will not be able to access your server any more. For guiding you in picking the best cipher suites for your OpenSSL version, we recommend Mozilla's SSL Configuration Generator.
Another way to increase the security of your HTTPS setup is to disable support for older SSL methods such as TLS v1.0 and v1.1. While as of April 2018 there are no known vulnerabilities specific to TLS v1.0 or v1.1, supporting only the newest standard will ensure better security through the use of more modern cipher suites.
In seeking the perfect balance between security and compatibility, you may wish to consider configuring only some services to have stricter cipher suites and/or TLS policy. These could be administration facing services such as the SFTPPlus Local Manager. For other services, you may need to adopt a policy that allows a compatible set as the default value for services such as HTTPS.
For example, here's the difference between secure and compatible SSL methods. Note that the secure method does not provide backward compatibility:
Secure methods: ssl_allowed_methods = tlsv1.2
This indicates that the server will only support TLS v1.2, and will not communicate with a client that supports only TLS v1.0 and/or TLS v1.1.
A more lenient set of SSL methods would be:
Compatible methods: ssl_allowed_methods = tlsv1.0 tlsv1.1 tlsv1.2
This indicates that the server will support clients using TLS version v1.2 and can communicate with clients that only support TLS v1.0 and/or TLS v1.1.
Beware that not supporting TLS v1.0 would mean dropping support for clients from older operating systems such as RHEL 5, SLES 11 and Solaris 10, as well as obsolete platforms like Android 4.0-4.3, Internet Explorer on Windows Vista and Win Phone 8.0, Java 7 clients. Anything using the old OpenSSL 0.9.8 version is also included.
Therefore, you may need to reach a compromise in choosing the ssl_allowed_methods too, and only restrict the SSL methods for the more sensitive services such as Local Manager.
Other resources to use
- Mozilla documentation from the OpSec team on Security and Server Side TLS
- SSL and TLS Deployment Best Practices
The details in this resource is for guidance only. Influences such as own security policies, requirements, and threat models should be considered when adopting this type of guidance.
This resource is written as of SFTPPlus version 3.33.0.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
Security Advisory on CSRF and XSS attacks affecting HTTP/HTTPS services
Tue 24 April 2018 | security
Customers using HTTP/HTTPS services should upgrade to 3.33.0
The SFTPPlus version 3.33.0 release is a major security update for the HTTP/HTTPS file transfer service and the SFTPPlus Local Manager service.
This update addresses the vulnerabilities concerning Cross-Site Request Forgery Attacks and Cross-Site Scripting Attacks on the aforementioned services.
Customers that are not accessing SFTPPlus services from a web browser are not exposed to these vulnerabilities.
In addition, customers utilizing FTP, FTPS, SFTP, and SCP protocols are not affected.
We recommend that all affected customers should upgrade to the SFTPPlus 3.33.0 release, since it includes fixes for Cross-Site Request Forgery and Cross-Site Scripting vulnerabilities.
To mitigate the risk in older SFTPPlus versions, we recommend the following actions:
- Do not have other tabs or windows open in the same browser while being authenticated to a SFTPPlus service, or
- Use a private window or a separate profile / container.
- Log out from the SFTPPlus service as soon as your have completed your tasks.
The aforementioned security issues were due to ProAtria not performing a security audit of SFTPPlus, when used from an interactive browser.
Taking into consideration the current challenges of HTTP security, we have now updated our security practices and implemented automated tests. These tests will cover the HTTP-specific attacks against SFTPPlus when accessed from a web browser.
SFTPPlus continues to be focused on automated, non-interactive file transfers in a secure fashion. Our security practices have been designed to make this a reality for our clients.
You can check the rest of the 3.33.0 release notes here.
SFTPPlus Release 3.33.0 now supports IPv6 server-side functionalities
Mon 23 April 2018 | security release
We are pleased to announce the latest release of SFTPPlus version 3.33.0.
This is a significant release in that it supports the Internet's next generation protocol, IPv6, for all server-side functionalities.
As we begin to hit the upper limit of IPv4 addresses, the current standard, what matters to us is to enable our customers and their businesses to set up their services on IPv6 with SFTPPlus.
In addition to IPv6 support, the following are new features and defect fixes associated with this release.
New Features
- A new authentication method was added which allows the server to read application accounts from a separate file. [server-side] [#1056]
- It is now possible to configure the supported ciphers for an SFTP location using the ssh_cipher_list configuration option. [#4619]
- The FTP and FTPS file transfer services now support IPv6 as specified in RFC 2428. [server-side][ftp][ftps] [#4823-1]
- The HTTP and HTTPS file transfer services now support IPv6. [server-side][http][https] [#4823]
- The event with ID 30011 now contains details about the encryption used by the SFTP and SCP connections. [server-side][sftp][scp] [#4850]
Defect fixes
- A defect was fixed in the SFTP service for the chmod operation. In previous versions, the chmod was ignored and always returned a success result. [server-side][sftp] [#4338]
- The HTTP PUT method of the file transfer service now returns a correct code when the HTTP request contains Expect: 100-continue and the request fails to be authenticated. [server-side][http][https] [#4856]
- When uploading files into an empty folder using a web browser which has Javascript enabled, you will now see the uploaded file in the folder listing. This issue was introduced in 3.31.0. This was not an issue for web browsers with Javascript disabled. [server-side][http][https] [#4865]
- The HTTP file transfer service will now force any file to be downloaded by the browser. Previously, it was displaying HTML or images inside the browser without forcing a download. [server-side][http][https][security] [#4877-1]
- The HTTP file transfer service and the Local Manager service were updated to prevent cross-site request forgery (CSRF / XSRF) attacks by validating the Origin and Referer headers against the Host header. [server-side][http][https][security] [#4877]
- The HTTP file transfer service will now set the session cookie using the httpOnly and 'sameSite' options. [server-side][http][https][security] [#4881]
- The error messages in the HTTP service were updated to prevent cross site scripting attacks (XSS). [server-side][http][https] [#4884]
You can check the full release notes here.
Data Loss Prevention - Systems, Software and Strategies
Thu 19 April 2018 | article infrastructure
What is Data Loss Prevention (DLP)?
Data Loss Prevention (or DLP for short) is the application of technology and policies in order to detect and prevent potential data breaches and data ex-filtration. Data that is of particular interest include sensitive emails, documents and other information leaving the organizational boundary. Data Loss Prevention is one out of many options used in today's arsenal of defense against threats and attacks, and also a layer to harden overall data security.
While SANS may write that DLP is primarily concerned with identifying sensitive data, we have taken on board a more holistic look beyond identification.
Data loss prevention can be in the form of the following:
- Network-based DLP.
- Endpoint DLP which monitors on the application level such as email client used.
- Network policies enforced for information leaving the network.
- UI, for example in the form of pop up tips, that will help reinforce data protection awareness training.
- Common dictionaries and regular expressions syntax used to create content protections rules.
- Staff awareness training.
- Using file tagging to secure data that can contain intellectual property or trade secrets.
The above is not an exhaustive list.
Data loss prevention tend to be interchanged with data leak prevention when the situation involves the lost data being acquired by an unauthorized third party. However for this article, we will also include both data loss and data leak scenarios under the overall DLP umbrella term.
Upon application of DLP, you can ensure compliance with regulations governing use of data and ensure obligations for best practices are being met. These compliance and regulations include Health Insurance Portability and Accountability Act (HIPAA), (Payment Card Industry) PCI compliance, and General Data Protection Regulation (GDPR) to name a few.
Data loss prevention in file transfers
Within the territory of file transfer, data loss happens via information being inadvertently or intentionally sent to an unauthorized individual through the use of either file transfer software or file transfer protocols. It can also happen due to human ignorance or negligence - for example, uploading sensitive documents using an unapproved cloud provider.
Imagine a scenario where an employee in a large company has just transferred a series of files containing confidential data. Or another scenario where a small business owner has data residing on USB (unencrypted) and has since been lost.
It is with these two scenarios where we see data loss prevention not being applied for both data in transit (the transfer of files containing confidential information) and data at rest (the files residing within the USB).
Types of data in file transfers
As an introduction, the following paragraphs (from Wikipedia) summarizes the differences between data at-rest, data in-use and date in-motion.
Data at-rest
"Data at rest" specifically refers to old archived information. This information is of great concern to businesses and government institutions simply because the longer data is left unused in storage, the more likely it might be retrieved by unauthorized individuals. Protecting such data involves methods such as access control, data encryption and data retention policies.
Data in-use
"Data in use" refers to data that the user is currently interacting with. DLP systems that protect data in-use may monitor and flag unauthorized activities. These activities include screen-capture, copy/paste, print and fax operations involving sensitive data. It can be intentional or unintentional attempts to transmit sensitive data over communication channels.
Data in-motion
"Data in motion" is data that is traversing through a network to an endpoint destination. Networks can be internal or external. DLP systems that protect data in-motion monitor sensitive data traveling across a network through various communication channels.
Data Loss Prevention and SFTPPlus MFT
DLP monitoring network activity
The DLP software is integrated into the network using a network TAP (terminal access point) port to perform real-time scanning and analysis of network traffic.
In addition to DLP inspection for data in-transit, DLP inspection can also be applied for data at-rest, such as within an FTPS or SFTP file server.
DLP and SFTPPlus MFT configuration options
For managed file transfer, data in-motion is of priority concern and is within the realm of control for file transfer software. Data at-rest is also another concern, but controls can also be distributed to controls permissioned by the OS file system.
The use of secure file transfer protocols as well as other processes for secure file transfer should form part of the stock for data loss prevention - transmission security. These services and configuration options can be configured using SFTPPlus.
An SFTPPlus feature, Digital signature validation can be configured to check if files have a valid signature:
SIGNED_CONTENT,SIGNATURE
The signature validation process is based on the RSA Digital Signature Algorithm PKCS#1 v2.1 also known as RSASSA-PSS and documented in RFC 3447.
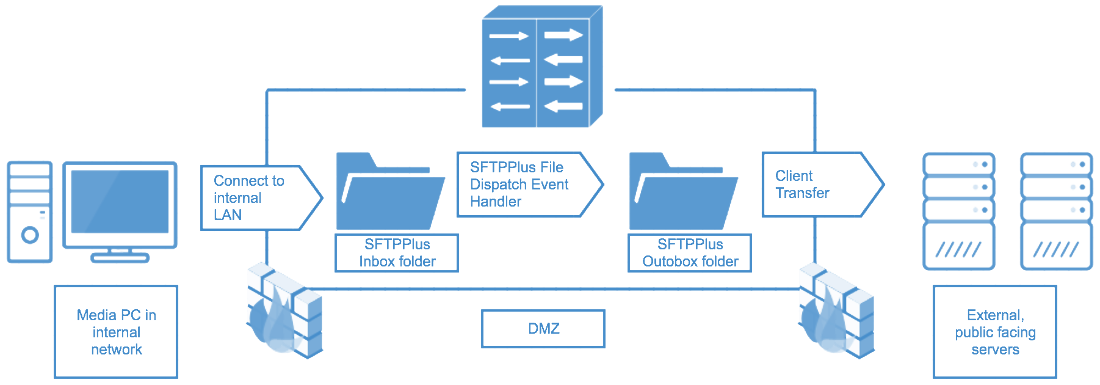
Post process actions may also be added as part of the automated, client transfer rule in order to contain policy rules. A file dispatcher can then be set so that a transfer is quarantined via a separate folder if it has failed a policy rule.
A UUID prefix can also be appended to a file name in order to create unique names so that for each data uploaded, even if duplicate, there is a unique filename.
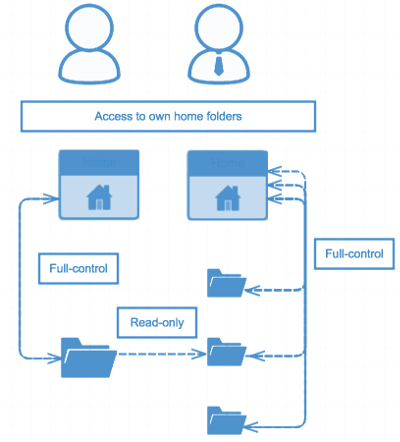
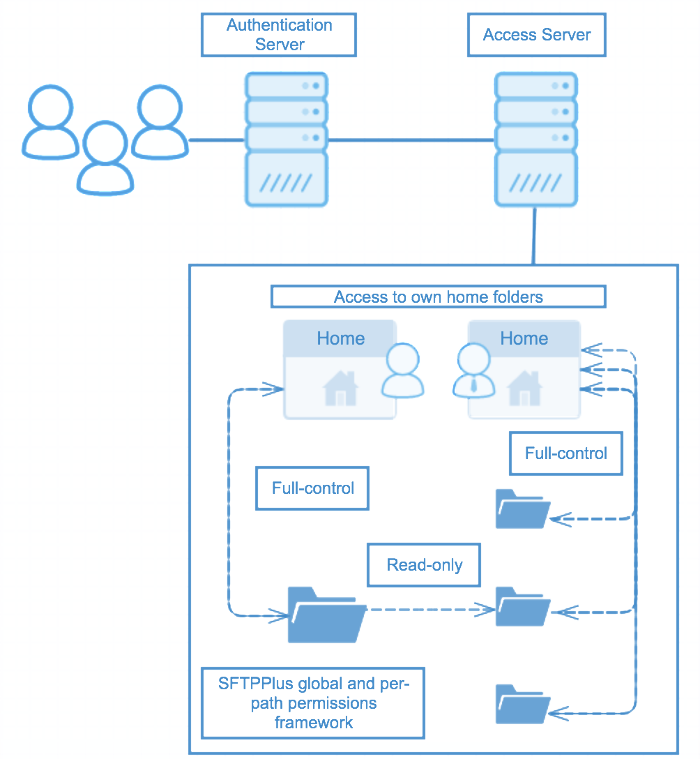
For authorization control, SFTPPlus administrators can apply permissions to specific groups or users. These permissions will help determine the access to which resources within the file transfer home directory of that user, and other the specific access rights. Permissions can also be set depending on regular expressions (regex), such as disallowing certain file formats. Through the options covered above, administrators can secure data or set permissions to ensure certain resources are not being inappropriately accessed or changed.
For more details about the above configuration options, please consult our documentation or talk to the Support team.
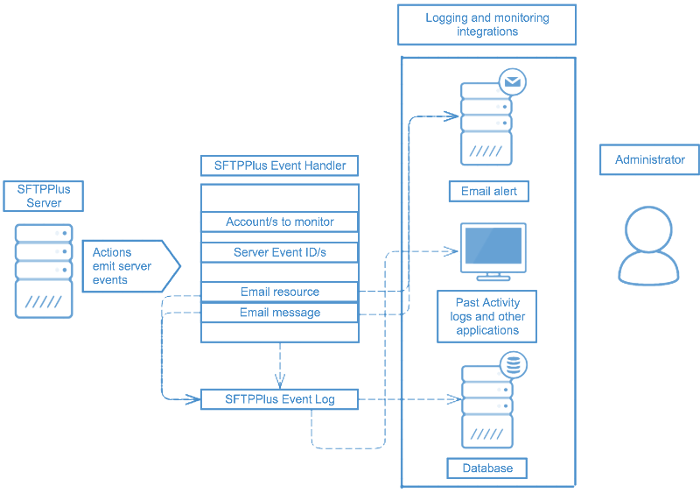
Audit trails for DLP
While operating, SFTPPlus will emit a set of events. Each event has a unique ID and defines a specific operation carried out by the server.
An example of an audit trail upon first connection to an FTP service is below:
| 20076 2018-03-07 19:44:05 ftp-only-1 Process 0.0.0.0:0 Service “ftp” started on “0.0.0.0:10023” using “ftp” protocol. | 10033 2018-03-07 19:44:10 ftp-only-1 Unknown 127.0.0.1:51290 New FTP/FTPS client connection made.
Administrators can gather a comprehensive picture of data-handling activities performed by users through the detailed, server-side audit trail. For example, see below audit trail for an attempt to access an authorized resource:
| 40007 2018-03-28 11:10:25 Process alice 127.0.0.1:52064 HTTP/HTTPS file access successfully started in "/ftps-folders/alice_files" as "/".
Through this online record of server events, organizations can be made aware for the purposes of any legal framework or compliance obligations.
Please see our Users Guides for specific examples pertaining to audit trails for HIPAA/HITECH, and GPG/PMO obligations. More articles are being written for other compliance and regulations.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus and its relevance with the OIAC Privacy Act and ASD ISM
Mon 16 April 2018 | australia compliance privacy
In this post, we outline two main compliance obligations relevant to Australia - the OIAC Privacy Act and the ASD ISM. For those familiar with other international compliance obligations, such as the GPG13 (Good Practice Guide) provided by the UK or HIPAA (Health Insurance Portability and Accountability Act) provided by the US, they will find the following information useful, especially when handling data and subsequent file transfers with Australian customers.
The following is just an introductory overview focusing on how SFTPPlus can help organizations with these obligations.
About the Privacy Act 1988
The Office of the Australian Information Commissioner (OIAC) administers the Privacy Act 1988. This Act is an Australian law which regulates the handling of personal information about individuals.
According to the OIAC, the Privacy Act includes thirteen Australian Privacy Principles (APPs). These APPs set out standards, rights and obligations for the handling, holding, use, access and correction of personal information including sensitive information. For more details, please refer to the OIAC website.
By ensuring that there is data in-motion encryption, such as the use of SFTP and FTPS in file transfers, organizations and businesses can ensure further security for their file transfers in order to help meet certain obligations indicated within the Privacy Act 1988.
About the ASD ISM
The Australian Signals Directorate (ASD), an intelligence agency in the Australian Government Department of Defence, has provisioned the Information Security Manual (ISM). Originally for government agencies to apply in order to protect ICT systems, the manual can also be of use for the private sector.
For the full documentation and details, please go to the ASD website. This page is based on the 2017 ISM Manual that was updated in November 2017.
Standard Operating Procedures (SOPs)
While the manual itself encompasses a wide range of topics from access controls to the use of ICT equipment, we have mapped components (SOPs) that is of direct or indirect relevance to file transfers involving SFTPPlus.
The following are Standard Operating Procedures (SOPs) as listed from page 36 of the ISM.
Access control
Procedure to be included: Authorising access rights to applications and data.
The SFTPPlus features that will help organizations meet this SOP include; ability to authorize access based on an existing authentication method (such as LDAP or operating system), ability to authorize or via an SFTPPlus application account.
Another example of rolling out proper access authorization is via permissions. User permissions can be set in the application based on extension (such as only making .exe files read-only) and directory (such as only allowing full control for certain folders).
Audit logs
Procedures to be included: Reviewing system audit trails and manual logs, particularly for privileged users.
For each server event that is emitted, this is logged within an audit trail that is available for SFTPPlus administrators. The example log below is of a user authenticating:
| 30014 2018-04-02 10:50:42 Process Unknown 127.0.0.1:50668 New SSH connection made. | 20137 2018-04-02 10:50:42 single-server-uuid 127.0.0.1:50668 Account "erica" of type "os" authenticated as "erica" by os authentication "Operating System Accounts" using ssh-key.
Note that details such as the date, time, type of connection, type of authentication, account name and more are included in this audit log.
Data Transfers
Procedures to be included: Managing the review of media containing information that is to be transferred off-site. Managing the review of incoming media for viruses or unapproved software.
For the thorough review of media containing sensitive information, it is expected that SFTPPlus be integrated with a DLP (data leak prevention) software and other related policies to help prevent data leaks.
For the review of incoming media, SFTPPlus can also be integrated with antivirus checks as part of a file transfer process.
Our own customers are already integrating with a number of software that monitors and protects the boundary as part of their file transfer infrastructure.
System integrity audit
Procedures to be included: Reviewing user accounts, system parameters and access controls to ensure that the system is secure. Checking the integrity of system software. Testing access controls.
The text configuration server.ini file is available to review all configurations - from the authentication methods, configuration parameters and configuration options right through to the services being used.
The SFTPPlus Local Manager also includes the ability to review any changes made, before applying it to the system.
System maintenance
Procedures to be included: Managing the ongoing security and functionality of system software, including; maintaining awareness of current software vulnerabilities, testing and applying software patches /updates / signatures, and applying appropriate hardening techniques
SFTPPlus upgrades are designed to minimize disruption.
Transport Layer Security (TLS) in the ISM
Page 250 of the ISM details these conditions under which TLS can be used, including FTP over TLS (or in other words, FTPS).
The FTPS service can be configured to ensure meeting this conditions - such as using tls v1.2. To meet the requirement of meeting Perfect Forward Secrecy as determined in page 251 of the ISM, SFTPPlus administrators can explicitly state which SSL ciphers to use. These are cipher suites that implement Perfect Forward Secrecy - Diffie–Hellman key exchange (DHE-RSA, DHE-DSA) or elliptic curve Diffie–Hellman (ECDHE-RSA, ECDHE-ECDSA). Administrators can use the secure configuration option to only ensure the SSL Cipher Suite configuration for the FTPS service is updated to only use the secure ciphers as recommended by the OpenSSL library.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Release 3.32.0
Thu 05 April 2018 | security release
We are pleased to announce the latest release of SFTPPlus version 3.32.0.
New Features
- SFTP and SCP file transfer services can now listen on IPv6 addresses and accept connections from IPv6 clients. [server-side][sftp][scp] [#1924]
- The HTTP and HTTPS service now accepts creating new folders with the HTTP PUT and WebDAV MKCOL methods. [server-side][http][https] [#4828-1]
- The HTTP and HTTPS service now accepts deleting folders and files with the HTTP DELETE method. [server-side][http][https] [#4828-2]
- The HTTP and HTTPS service now accepts file uploads using the HTTP PUT method. [server-side][http][https] [#4828]
Defect fixes
- FTP and FTPS client side transfer can now transfer files larger than a few bytes from a remote FTP/FTPS server and to the local filesystem. This issue was introduced in SFTPPlus version 3.20.0. This defect was not affecting uploading / pushing files to a remote FTP/FTPS server. [client-side][ftp][ftps] [#4754]
- The Developer Documentation for the HTTP authentication method was updated to make it clear the expected repose codes for the authentication server. [server-side] [#4758]
- The JavaScript UI for the HTTP and HTTPS file transfer services no longer limit the file size to 256MB. This defect was introduced in 3.31.0. [server-side][http][https] [#4815]
Deprecations and Removals
- The default secure ssl_cipher_list configuration was updated to HIGH:!PSK:!RSP:!eNULL:!aNULL:!RC4:!MD5:!DES:!3DES:!aDH:!kDH:!DSS. The previous value was ALL:!RC4:!DES:!3DES:!MD5:!EXP. In this way, when updating the OpenSSL library you will automatically get an update in the list of secure ciphers, without the need to update SFTPPlus. [security][ftps][https][client-side][server-side] [#4748]
- The event (ID 40025) that was emitted when an unknown error was generated by the HTTP service during a JSON API request was removed. It has been replaced with event ID 40003. [server-side][http][https] [#4828]
You can check the full release notes here.
Understanding the exchange between SFTP Client and SFTP Server
Thu 08 March 2018 | article
Why read this?
As part of meeting the Accounting component of the AAA (Authorization, Authentication and Accounting) framework, each event and action on the server and/or the client-side are recorded by SFTPPlus. These events have an associated Event ID which is also publicly searchable both on our website and on the internal documentation included in the software package that you have downloaded.
System and network administrators touching on logs - be it in the most verbose format or not - may find this article describing the breakdown of such logs helpful.
For this example, we will be touching on SFTPPlus SFTP transfers from both the client-side and server-side only. Please do not hesitate to get in touch with us if you are interested in learning more about other file transfer protocols.
This article was written as of SFTPPlus version 3.31.0.
SFTPPlus SFTP Server-side Perspective
Initial configuration notes
If you are currently evaluating SFTPPlus, please follow our documentation to learn more about how you can configure your database and event handlers to suit your specifications.
Read more about configuring databases with SFTPPlus.
Read more about configuring event handlers. These provide further ways to configure SFTPPlus to create logging actions based on the events recorded.
Even if you are an existing customer, you can follow our documentation links above in order to refresh your knowledge on configuring SFTPPlus version 3. For those on legacy versions, please consult the documentation relevant to your version.
Example logs from SFTPPlus
The following are snippets when logging in for the first time from a GUI client to an SFTPPlus 3.30.0 SFTP server.
A new connection has been made to the service sftp-1. Knowing the service name is useful in case there are multiple other SFTP services running:
| 30014 2018-02-27 17:28:53 sftp-1 Unknown 127.0.0.1:58032 New SSH connection made. | 2018-02-27 17:28:53 30014 New SSH connection made.
The following are authentication methods associated with the server and confirmation of which methods are not active. There may be more methods, depending on how many of these are set up and enabled. To simplify the login process, please make sure to disable all unused authentication methods.:
| 20138 2018-02-27 17:28:55 some-http-auth-uuid Unknown 127.0.0.1:58032 Ignoring http authentication "auth-over-remote-http" for "user" since it is not active. | 2018-02-27 17:28:55 20138 Ignoring http authentication "auth-over-remote-http" for "user" since it is not active. | 20138 2018-02-27 17:28:55 ldap-uuid Unknown 127.0.0.1:58032 Ignoring ldap authentication "LDAP against local test server" for "user" since it is not active.
The following logs list out a successful authentication of user using the ssh-key:
| 20137 2018-02-27 17:28:55 test-server-uuid Unknown 127.0.0.1:58032 Account "user" of type "application" authenticated as "user" by application authentication "Application Accounts" using ssh-key. | 2018-02-27 17:28:55 20137 Account "user" of type "application" authenticated as "user" by application authentication "Application Accounts" using ssh-key.
The following log message confirms the type of permissions allowed for the account and an active transfer that is already running:
| 20182 2018-02-27 17:28:55 Process user 127.0.0.1:58032 Account "user" logged in with permissions [[u'allow-full-control'], [u'/main_folder/*', u'allow-full-control'], [u'*.PDF', u'allow-read']]. Files uploaded as: test.txt
The following confirms that the user has logged into and now has access to the folder as the root ("/") folder:
| 30011 2018-02-27 17:28:55 Process user 127.0.0.1:58032 Subsystem SFTP successfully started in "/root/home/node/user/" as "/". | 2018-02-27 17:28:55 30011 Subsystem SFTP successfully started in "/root/home/node/user/" as "/". | 30060 2018-02-27 17:28:55 Process user 127.0.0.1:58032 Canonical file name requested for ".". | 2018-02-27 17:28:55 30060 Canonical file name requested for ".". | 30060 2018-02-27 17:28:55 Process user 127.0.0.1:58032 Canonical file name requested for "/.". | 2018-02-27 17:28:55 30060 Canonical file name requested for "/.". | 30019 2018-02-27 17:28:55 Process user 127.0.0.1:58032 Listing folder "/". | 2018-02-27 17:28:55 30019 Listing folder "/". | 30020 2018-02-27 17:28:55 Process user 127.0.0.1:58032 Successfully listed folder "/". | 2018-02-27 17:28:55 30020 Successfully listed folder "/".
SFTPPlus SFTP Client-side Perspective
Initial configuration notes
If you are currently evaluating SFTPPlus, please follow our client side documentation.
The SFTPPlus Client software utilizes the command-line client-shell to access remote file servers using the interactive shell.
Even if you are an existing customer, you can follow our documentation links above in order to refresh your knowledge on configuring SFTPPlus version 3. For those on legacy versions, please consult the documentation relevant to your version.
Example logs from SFTPPlus
Let's connect with SFTPPlus Client using the SFTP protocol on port 10022. The following log details the UUID of the sftp service and confirms the connections:
| $ ./bin/client-shell.sh sftp://user@localhost:10022 -p pass --ssh-server-fingerprint 06:cb:46:2b:9a:9a:c4:10:54:f0:ea:2f:b6:05:cb:a0 | SFTPPlus (3.31.0) file transfer client shell | > connect | 20140 2018-03-05 16:40:59 51e1db00-8214-4b68-96fe-58470b8b2fc5 Process 0.0.0.0:0 Connecting resource "sftp". | 30072 2018-03-05 16:40:59 Process user localhost:10022 Location sftp connected to the SSH server. | 30076 2018-03-05 16:40:59 Process user localhost:10022 Client SFTP subsystem initialized for location sftp. | 20141 2018-03-05 16:40:59 51e1db00-8214-4b68-96fe-58470b8b2fc5 Process 0.0.0.0:0 Resource "sftp" successfully connected. | 20156 2018-03-05 16:40:59 51e1db00-8214-4b68-96fe-58470b8b2fc5 Process 0.0.0.0:0 Successfully started location "sftp" of type sftp.
On the event that the SFTP connections fails, the log will state a number of details. The event ID is 30073. The event will communicat the host key algorithm that is in use to identify the server-side, the cipher used to receive data, the HMAC for both sent and received data, key exchange algorithm, cipher used for sent data and the name of the location associated for this event. Below is an example of the event that has been emitted has part of this new SFTP connection.:
| 30073 2018-03-05 16:36:16 Process user localhost:10022 Connection to SSH server was lost for location sftp. Protected using host-key:ssh-rsa key-exchange: diffie-hellman-group-exchange-sha256 in-hmac:hmac-sha2-256 in-cipher:aes256-ctr out-hmac:hmac-sha2-256 out-cipher:aes256-ctr
Providing that the SFTP connection succeeds, supported actions are logged as either a success like below:
| > gattrs remote_get | 60071 2018-03-05 16:41:22 Process Process 0.0.0.0:0 Successfully got attributes for "Reports_2018" on "sftp". | name: Reports_2018 | path: Reports_2018 | size: 128 | modified: 2018-02-16 16:15:21 | is_file: False | is_folder: True
Or error details are caught with an explanation message as to why:
| > get unknown_file
| 20145 2018-03-05 16:42:08 Process Process 0.0.0.0:0 Failed to resolve
text for event id "60054" with data "{'path': 'unknown_file\xc8\x9bu',
'location': u'sftp', 'avatar':
<chevah.server.identity.avatar.ProcessAvatar object at 0x10efc3110>,
'details': "'ascii' codec can't decode byte 0xc8 in position 9: ordinal
not in range(128)"}". 'ascii' codec can't decode byte 0xc8 in position
9: ordinal not in range(128)
SFTPPlus SFTP Exchange - Detailed Verbose OpenSSH Logs
Initial configuration notes
Following from that, you can use the built-in the client-side or server-side software that you are utilizing. SFTPPlus offers logging functionalities both for the client-side and server-side. Network administrators using other software, such as sftp -vvv, for client or server may wish to use additional logging functionalities.
Example with sftp -vvv output
These lines mean that SSH protocol 2.0 is being utilized with the version of OpenSSH:
debug1: Enabling compatibility mode for protocol 2.0 debug1: Local version string SSH-2.0-OpenSSH_7.6
This line indicates which protocol version is in use service-side and which version:
debug1: Remote protocol version 2.0, remote software version SFTPPlus_3.30.0
This indicates which algorithms are preferred. You may opt to only select the strongest availability supported in your system first. In this case the ordering is logical as it moves from the more secure algorithm down to a less secure algorithm.:
| debug3: order_hostkeyalgs: prefer hostkeyalgs: ssh-rsa-cert-v01@openssh.com,rsa-sha2-512,rsa-sha2-256,ssh-rsa
These are the key exchange algorithms that are available.:
| debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org, ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521, diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512, diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1, diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,ext-info-c
These are the host key algorithms.:
| debug2: host key algorithms: ssh-rsa-cert-v01@openssh.com,rsa-sha2-512, rsa-sha2-256,ssh-rsa,ecdsa-sha2-nistp256-cert-v01@openssh.com, ecdsa-sha2-nistp384-cert-v01@openssh.com, ecdsa-sha2-nistp521-cert-v01@openssh.com,ssh-ed25519-cert-v01@openssh.com, ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,ssh-ed25519
These are the ciphers used from client to server (ctos) and from server to client (stoc):
| debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr, aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com | debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr, aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
These are the ciphers used from client to server (ctos) and from server to client (stoc):
| debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com, hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com, hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com, hmac-sha2-256,hmac-sha2-512,hmac-sha1 | debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com, hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com, hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com, hmac-sha2-256,hmac-sha2-512,hmac-sha1
These are the compression algorithms used from client to server (ctos) and from server to client (stoc):
debug2: compression ctos: none,zlib@openssh.com,zlib debug2: compression stoc: none,zlib@openssh.com,zlib
This is the key exchange initialized proposal from the host server:
| debug2: peer server KEXINIT proposal | debug2: KEX algorithms: diffie-hellman-group-exchange-sha256, diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1, diffie-hellman-group14-sha1 | debug2: host key algorithms: ssh-dss,ssh-rsa | debug2: ciphers ctos: aes256-ctr,aes256-cbc,aes192-ctr,aes192-cbc,aes128-ctr,aes128-cbc, 3des-ctr,3des-cbc | debug2: ciphers stoc: aes256-ctr,aes256-cbc,aes192-ctr,aes192-cbc,aes128-ctr,aes128-cbc, 3des-ctr,3des-cbc | debug2: MACs ctos: hmac-sha2-256,hmac-sha1 | debug2: MACs stoc: hmac-sha2-256,hmac-sha1 | debug2: compression ctos: none,zlib | debug2: compression stoc: none,zlib
These are the key exchange algorithms used from server to client and client to server:
| debug1: kex: algorithm: diffie-hellman-group-exchange-sha256 | debug1: kex: host key algorithm: ssh-rsa | debug1: kex: server->client cipher: aes128-ctr MAC: hmac-sha2-256 compression: none | debug1: kex: client->server cipher: aes128-ctr MAC: hmac-sha2-256 compression: none
This is the SSH version 2 key exchange Diffie-Hellman Group Exchange request. This specifies the size of the SSH prime moduli being calculated by the SFTP server as indicated in the SFTPPlus /configuration/ file. When you first initialize SFTPPlus version 3, the Time Type Tests Tries Size Generator Modulus is generated and saved in ssh-service.moduli. This file contains primes ranging in size from 1023 to 8191 bits. An example of the contents for the .moduli file is below:
| 20060827134212 2 6 100 3071 2 D3230D237572ECE9F92358715EBAC3A4D89F2D6B4DC39F056450263BEF1665FBD 7B93916ABC867B7064802159D273C7EB01C5F9281A3D6DCCB7CF997D385998EC0E1FA3319AFE771A90ADBACEB414A02 0630D7C7F161FAFEC6C9FC06D3205C712AAE8848A1B2C21DFF301C7FFC0B75D13F060A313C32AFEEAF1493F641760EB EF38829B3371699D2A3264D0ECEB4E5C19581ED8C57699F559B9828BBFE147952E289F0E171C9C60335DD2F492CB409 A4DB97BDF86E2DBA605064DB040A3DF5678E24F66718CA115C95C892FF7AEDFAABC2E6414716298CEC1A604270FEADF 191B7C8A59C238C395A65442C0B963BF83025BED3951A271B7440EC7687C31DE63355DA7FEAC15DC962C7BF7614EB59 B077B9889AD8703DFE98AC99615B722A0ABE89956D1058E025C7733420CB51D7E1608EFF2C0A30C9A5EB77CCA02C6B0 0CE781B172001C6C458630890062E27CE307D513A7686A69D1D548DE8334B13136D9E842A5E17FD67522C93823E03F0 8AEE8024AF5D88B2EE01D4D9980084EFD5D943
In the following example below, a SSH moduli prime from 2048 to 8192 bits are used. Specifically, a moduli with a range from 4092 to 8192 are sent for the SSH message key exchange Diffie-Hellman group exchange request as indicated on debug1 line below (SSH2_MSG_KEX_DH_GEX_REQUEST(2048<8192<8192)) Once sent, the server uses the moduli file, the same file that was initialized as part of the SFTPPlus installation steps, in order to crack the shared secret. The server provides its host key back to the client along with the algorithm used as indicated by the final line as Server host key: ssh-rsa SHA256:hdSfa7gb2O984malHerkwerj3m20dHb6Yuwl0&hbxFj.
See the rest of the output below:
| debug1: SSH2_MSG_KEX_DH_GEX_REQUEST(2048<8192<8192) sent | debug3: receive packet: type 31 | debug1: got SSH2_MSG_KEX_DH_GEX_GROUP | debug2: bits set: 4092/8192 | debug3: send packet: type 32 | debug1: SSH2_MSG_KEX_DH_GEX_INIT sent | debug3: receive packet: type 33 | debug1: got SSH2_MSG_KEX_DH_GEX_REPLY | debug1: Server host key: ssh-rsa SHA256:hfSfa0gb2O884malLerkwerj3m20dBb6Yuwl0&hbxGj
The client then checks to see if the host key is located within the known_hosts file:
| debug3: hostkeys_foreach: reading file "/root/home/node/.ssh/known_hosts" | debug3: record_hostkey: found key type RSA in file /root/home/node/.ssh/known_hosts:8 | debug3: load_hostkeys: loaded 1 keys from [12.345.678.90]:10022
A few more steps occur to verify this server host name and port:
ddebug1: Host '12.345.678.90]:10022' is known and matches the RSA host key. ddebug1: Found key in /root/home/node/.ssh/known_hosts:8
This is the server rekey interval:
debug1: rekey after 4294967296 blocks debug1: SSH2_MSG_NEWKEYS sent debug1: expecting SSH2_MSG_NEWKEYS debug3: receive packet: type 21 debug1: SSH2_MSG_NEWKEYS received debug2: set_newkeys: mode 0 debug1: rekey after 4294967296 blocks
The following are SSH keys found:
debug2: key: imported-openssh-key (0x7e403ff95550), agent debug2: key: /root/home/node/.ssh/id_rsa (0x0) debug2: key: /root/home/node/.ssh/id_dsa (0x0) debug2: key: /root/home/node/.ssh/id_ecdsa (0x0) debug2: key: /root/home/node/.ssh/id_ed25519 (0x0)
The following are authentication methods that can continue, the preferred authentication order, remaining preferred:
| debug3: send packet: type 5 | debug3: receive packet: type 6 | debug2: service_accept: ssh-userauth | debug1: SSH2_MSG_SERVICE_ACCEPT received | debug3: send packet: type 50 | debug3: receive packet: type 51 | debug1: Authentications that can continue: password,publickey | debug3: start over, passed a different list password,publickey | debug3: preferred publickey,keyboard-interactive,password | debug3: authmethod_lookup publickey | debug3: remaining preferred: keyboard-interactive,password | debug3: authmethod_is_enabled publickey | debug1: Next authentication method: publickey | debug1: Offering public key: RSA SHA256:F8zPRFytcYU8PERggkPDs+D32TRgvVm4H3BBJduo+de /root/home/node/.ssh/id_rsa | debug3: send_pubkey_test | debug3: send packet: type 50 | debug2: we sent a publickey packet, wait for reply
The server will go through the exchange to authenticate until the final preferred method is reached - the password method. Upon success, the client enters an interactive session with the server.
There will also be additional verbose logs after entering an interactive session, such as a brief snippet below:
debug2: fd 6 setting TCP_NODELAY debug3: ssh_packet_set_tos: set IP_TOS 0x08 debug2: client_session2_setup: id 0 debug1: Sending environment. debug3: Ignored env _system_type debug1: Sending env LANG = en_CA.UTF-8 debug2: channel 0: request env confirm 0 debug3: send packet: type 98 debug3: Ignored env _system_arch debug3: Ignored env XPC_FLAGS debug3: Ignored env _system_version debug3: Ignored env XPC_SERVICE_NAME debug3: Ignored env rvm_version debug3: Ignored env _system_name debug1: Sending subsystem: sftp
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
Protecting your SFTPPlus configuration against SWEET32
Fri 02 March 2018 | security
Details of attacks on DES (Data Encryption Standard) and Triple DES, Birthday attacks on 64-bit block ciphers were released with the CVE ID of CVE-2016-2183. Read more about the CVE details here).
DES and Triple DES ciphers, used in TLS and SSH protocols and in subsequent relation also used in file transfer products, have a birthday bound of approximately four billion blocks. This makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted session, as demonstrated by an HTTPS session using Triple DES in CBC mode. This attack is otherwise known as the "SWEET32" attack.
If your SFTPPlus configuration is vulnerable to these attacks, you will need to ensure that you are on the latest SFTPPlus MFT version 3.xx.xx series and use the following custom configurations outlined below.
From SFTPPlus version 3.31.0, you can use the secure cipher option for the ssl_cipher_list and ssh_cipher_list configurations. The special keyword secure contains all the algorithms that we currently consider secure.
From version 3.32.0, the default secure ssl_cipher_list configuration was updated to HIGH:!PSK:!RSP:!eNULL:!aNULL:!RC4:!MD5:!DES:!3DES:!aDH:!kDH:!DSS where HIGH is defined by upstream OpenSSL.
In this way, when updating the OpenSSL library, you will automatically get an update in the list of secure ciphers without the need to update SFTPPlus.
Exclude DES and Triple-DES from the SSL Cipher List
SFTPPlus relies on OS crypto for the SSL/TLS portion. There is no need to run this configuration if your operating system has already deprecated the use of DES/3DES.
To check if your OpenSSL has DES and 3DES ciphers enabled, check the output of openssl ciphers -v 'DES:3DES'
If DES/3DES are still available in OpenSSL, disable them for SFTPPlus by ensuring that the ssl_cipher_list configuration for the service has the value :!DES:!3DES: added in the list. This will exclude the use of DES and Triple DES as indicated by the ! mark.
For more details about this configuration, please refer to the ssl cipher list configuration option here.
Exclude DES and Triple-DES from the SSH Cipher List
In the ssh_cipher_list configuration for the service, add the value :!DES:!3DES: to exclude the use of DES and Triple DES. There is no need to run this configuration if your operating system has already deprecated the use of DES/3DES.
More details about this configuration for the ssh cipher list here.
Only use TLS 1.2 (for services utilizing TLS/SSL)
In the ssl_allowed_methods option for the associate service, add the value tlsv1.2 to use TLS v1.2.
Ensure that tlsv1.2 is the only value in ssl_allowed_methods so that this component will use TLS v1.2 during the secure communication handshake.
DES ciphers are used in TLS 1.0 and TLS 1.1, but they are not available in TLS 1.2 as noted in RFC 5469.
In the event that you still require communication with services still utilizing TLS 1.1 and/or TLS 1.0, you may add tlsv1.1 and/or tlsv1.0 providing that the DES and Triple-DES ciphers are excluded in the first instance.
More details about this configuration are available in our documentation here.
Confirming the SFTP configurations using openssl s_client
You can use openssl s-client, a diagnostic tool.
Connect via openssl s_client -cipher 3DES -connect site:port to check that 3DES is disabled.
To check the TLS version, the output will also reveal which TLS version is being used:
SSL-Session:
Protocol : TLSv1.2
Cipher : 0000
Session-ID:
Session-ID-ctx:
Master-Key:
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1519733544
Timeout : 300 (sec)
Verify return code: 0 (ok)
Confirming the FTPS configurations using curl
If you wish to use curl instead, there are two tests that you can run once these options are saved in your development lab.
Run curl with the excluded ciphers DES-CBC3-SHA and check that you cannot complete the operation.
curl -v --ftp-ssl -k ftp://user@domain:port --ciphers DES-CBC3-SHA
Run curl with the allowed TLS version and check that you are able to complete the operation.
curl -v --ftp-ssl -k ftp://user@domain:port --tlsv1.2
Using --tlsv1.0 should fail the operation.
Confirming the configuration from the log
SFTPPlus configurations can also be confirmed via the log. For this issue, it should be done more as a supplementary step rather than as a sole point of confirmation of your configuration changes.
From the client-shell:
| SFTPPlus (3.30.0) file transfer client shell | > connect | 20140 2018-02-04 10:23:03 uuid Process 0.0.0.0:0 Connecting resource "ftpse". | 10102 2018-02-04 10:23:03 uuid user localhost:10021 Location ftpse connected to the FTP server. | 10106 2018-02-04 10:23:03 uuid user localhost:10021 Connection to FTP/FTPS was authenticated for location ftpse. Protected using TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384. Server certificate: (4) C=UK/O=ACME/CN=myserver.
From the server-side log:
| 10059 2019-06-18 09:42:36 ftp-1 johnd 127.0.0.1:48218 User successfully logged on "/users/John_D" as "/". Command protected using TLSv1.2 ECDHE-RSA-CHACHA20-POLY1305. Client certificate: (2) C=GB/O=ACME/CN=myclient
The logs above indicate that TLSv1.2 was used alongside the list of ciphers ECDHE-RSA-AES256-GCM-SHA384. Please note that just because TLSv1.2 is used, it does not indicate that other TLS versions are disabled.
Relevant documentation links
View the Security Users Guide offering a SSL / TLS / SSH protocols overview.
View the Users Guide for working with SSL certificates, PKI and CA.
View the SWEET32 website published by the two researchers, Karthikeyan Bhargavan and Gaëtan Leurent.
This article was written as of SFTPPlus version 3.32.0.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus is not affected by the Meltdown and Spectre Vulnerabilities
Wed 21 February 2018 | article security
Security advisory about the Meltdown and Spectre are vulnerabilities
Meltdown and Spectre are vulnerabilities based on CPU design flaws which require the attacker to be able to execute application code which is created to exploit these vulnerabilities.
SFTPPlus secure file transfers does not allow any arbitrary application code execution. It will only read and write data without executing it. This is standard behaviour for doing file transfers over FTPS or HTTPS.
The SSH implementation of SFTPPlus is only allowed for the SFTP and SCP protocols. Shell access or any other SSH execution is denied. The SCP protocol is implemented using an embedded SCP protocol and no external scp application is called.
For the purpose of managed file transfers, SFTPPlus allows the execution of pre-configured application code with the pre and post transfer hooks. As long as the SFTPPlus is configured with trusted applications, this does not constitute an attack vector.
If you are running SFTPPlus Itanium architectures, for example with HPUX, you are not affected by these vulnerabilities, no mater what other software is in used on those systems.
SPARC architecture (example with Solaris 10) and POWER (example with AIX 7.1) are affected by the Spectre, while not being affected by Meltdown.
The embedded devices based on ARM64 CPUs are also affected by Spectre.
Administrators using the SFTPPlus MFT Client with pre and post transfer hooks should review the configuration and make sure that the hooks will trigger calls to trusted applications.
This article was written as of SFTPPlus version 3.31.0.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Release 3.31.0
Tue 20 February 2018 | security release
We are pleased to announce the latest release of SFTPPlus version 3.31.0.
New Features
- The option to enforce unique names for uploaded files is now available for the HTTP and HTTPS file transfer services. [server-side] [#4465]
- A SOCKS version 5 (SOCKS5) proxy without authentication can now be used to connect to remote SFTP and SCP servers. [client-side][sftp][scp] [#4546]
- A new event handler option is added in order to send filtered events to standard output. This can be used when running SFTPPlus in Docker or with other process supervisors. [#4645]
- The option to enforce unique names for uploaded files is now available for the FTP, Implicit FTPS and Explicit FTPS protocols. [server-side] [#4650]
- The file-dispatcher event handler can now be configured to automatically create destination folders. [#4652]
- The close event description for SFTP and SCP client-side and server-side connection now contains the encryption used to protect connection. [client-side][server-side][sftp][scp] [#4668]
- The HTTP and HTTPS file transfer services now allow uploading multiple files and adding files via drag and drop. [server-side][http][https] [#4673]
- Support for Red Hat Enterprise Linux versions 7.0 to 7.3 with OpenSSL 1.0.1 was readded alongside support for RHEL 7.4 and newer using OpenSSL 1.0.2. [#4691]
- A new secure configuration value is available for the ssl_cipher_list and ssh_cipher_list as part of the FTPS, SFTP, SCP, and HTTPS file transfer services. [security][client-side][server-side] [#4727]
Defect fixes
- The transfer for SFTP and SCP locations is no longer interrupted when the remote server is requesting a SSH re-key exchange. This was affecting client-side transfers of files bigger than 1GB, as this is the point where some servers are re-keying. This is when either side forces the other to run the key-exchange phase which changes the encryption and integrity keys for the session. [client-side] [#4302]
- It is now possible to stop the client shell at any time by pressing the Ctrl+C key combination. In previous versions this was not available while an operation was in progress. [#4626]
- The AIX 7.1 build of SFTPPlus was updated to work with older OpenSSL versions. Previous versions of SFTPPlus (from 3.27.0 to 3.30.0) on AIX 7.1 required OpenSSL 1.0.2k or newer. [#4696]
- SFTP and SCP client and server side can now handle key exchange process even for peers which advertise their SSH version string with trailing spaces. This can happen for Bitvise SSHD Server when configured to omit its version. [client-side][server-side][sftp][scp] [#4718]
- The documentation for expression matching was updated to explain that regular expression matching is done as a search operation. For an exact match, use the start and end regex anchors. [#4724]
Deprecations and Removals
- Events with ID 40015 and 40016 were replaced by already existing event with ID 40022. Event 40022 is now the only one emitted when there are errors during an upload operation. [server-side][http] [#4465]
- The default configuration for SFTP, SCP, FTPS, and HTTPS connections was updated to exclude the 3DES cipher in order to prevent SWEET32 attacks. To not break backward compatibility for existing installations, this change affects only new installations. Existing installations will need to be manually updated to exclude the 3DES based ciphers. [#4727]
You can check the full release notes.
Tips to managing your file transfer requirements
Fri 16 February 2018 | article
Designing a file transfer system can be a difficult task. Which file transfer protocols should I use? Do I need server-side or client-side software or both? How do I authenticate my file transfer users securely?
Your first step in this journey is to understand your requirements. In this post, we summarize the requirements into sections for you to consider and think about.
After you have determined these requirements, feel free to contact the team or sign up for your evaluation of SFTPPlus MFT below!
Assess your requirements for a file transfer software
The first step is to list down all of your requirements for file transfer technology. While this may be obvious, there may be some items that you have not even considered when hunting for options.
1. What are your protocol requirements?
There are a number of file transfer protocols in place, with certain protocols being more secure than others. We have a guide about file transfer protocols which will help you make more informed decisions.
2. What are your workflow requirements?
Will the file transfer software be able to sync with your current workflow? Will there be any impediments or considerations that need to be taken into account when migrating your workflow into a file transfer solution? Will you be automating any transfer scenarios?
It is questions like these where it helps to get in touch with our Support team with your transfer scenarios. And from there, we can convert these scenarios into the basis of an actual configuration for you to use with our software.
3. What are your programmability requirements?
Will you require access to the API and will the developers be knowledgeable of the API codebase? What are your integration requirements that is required to be programmed as part of the file transfer solution?
4. What are your security requirements?
Will you require an AV programme to run post-process actions after transfers? Will you be able to specify exactly which ciphers should be used? Will the file transfer software meet your AAA framework? Having these requirements in mind will help meet your organization's security goals and will also help us in ensuring that the software is delivered in the most secure manner as possible.
5. What are your operational requirements?
Does the file transfer software support your operating system? Are there any upgrades required in order to run the required packages? Can the software be integrated with resilient and highly available systems?
These five questions are just the beginning in terms of thinking about your file transfer requirements. Please read on for more advice.
Assess proprietary or non-proprietary solutions
Do you require a solution with vendor lock-in and only proprietary protocols? If you are looking for a solution that has vendor lock-in, then you may want to think twice and reconsider the benefits of open standards.
SFTPPlus operates with open and standard protocols, as supported by RFCs, making portability an ease when moving between using one protocol (such as FTPES) in favor of another (such as SFTP).
With the use of permissive free frameworks, such as Twisted Python, our developers also contribute to the upstream libraries that we use.
SFTPPlus is supported across both proprietary (such as Windows) and non-proprietary OS' (such as FreeBSD). The list of supported platforms are available here.
Optimize performance with costs
In terms of costs, SFTPPlus marks at the more affordable side with the focus on being cost effective while also delivering a high-end functional product. While there are larger software suites available on the market, many of these incorporate a number of overhead and other additional costs in order to operate that is not related to the file transfer software itself. Our focus is only on delivering our main product offering and services in secure file transfer and to deliver it well.
Consider the IT infrastructure that will house your file transfer system
You will want to select an option that will integrate with your current IT workflow requirements.
If your users are already authenticating with Windows Domain Accounts on servers running Active Directory, then you will want to use the same authorization mechanism for authorizing file transfer users.
Will you be implementing file transfers within specialized environments such as a high availability network?
Part of your IT infrastructure may also include legacy systems. Are you running on Unix system or do you need an SFTP server for your AIX system? Or what about Solaris 10 which has OpenSSL 0.9.7? Our software has integrated with the above requirements, and more.
Choosing a solution that suits and integrates with your existing IT infrastructure will also reflect positively on sunk costs in terms of still being able to maintain operations with these infrastructures.
Investigate how file transfers will be initiated
Will you be searching for a proactive or a reactive solution? Will you be looking to initiate file transfers (for example, via a user logging in) or will the solution require the transfer to be initiated (for example, by a rule or an event)?
What types of transfer scenarios will you be working with? Push scripts? Pull scripts? Will there be additional processing required?
What types of rules do you need support for the file transfers? Will there be events-based rules? Scheduling? Will there be a filter requirement?
With managed file transfer, you can set many rules to initiate a transfer and automate these actions. If you have not faced these requirements until now, feel free to contact the Support team with your questions and scenarios.
Figure out your authorization, accounting and auditing implementation
Similar to considering the existing IT infrastructure, you will also need to figure out that your authorization, account and auditing implementation is supported by the secure file transfer software.
Will the accounts be authorized with the correct set of permissions?
Will you be able to utilize existing authentication mechanisms with the file transfer product?
Will you be able to conduct the appropriate auditing as required for compliance and obligations purposes?
All of these requirements should be on the table while searching for a secure file transfer solution.
Evaluate options to further secure your file transfer system
Compliance is a requirement for a number of organizations today, especially in regulated industries such as banking and healthcare. You will need to enquire to see if the secure file transfer product has features in place to help with compliance. Whether it is only allowing FIPS 140-2 ciphers, ensuring that you are compliant with PCI or GDPR standards, or checking that the audit trail is HIPAA compatible, you will want to ensure that the options to be compliant and secure are available to you.
What is the approach to quality assurance?
How is the secure file transfer tested? Is it run against an automated test suite, manually tested with smoke test scenarios? Is it tested against the platform that you are using?
What considerations do you also need to undertake testing from your test lab? Soak, systems integration and unit integration testing may also be required. This is to evaluate the file transfer product as an additional check to see that it meets the actual systems, environments, processes and interactions that are specific to your requirements.
Consider any required upgrade paths for the future
While this requirement may be far from your mind when you are looking for a new solution, you may want to take note of what the required upgrade paths are.
How will you export the configuration from one system to another? What happens if an OS upgrade or a patch is made to a system?
Our upgrade paths are well documented and we work with our customers that are working on upgrading their systems that may affect the file transfer component. We have worked with many scenarios - whether it is a full OS upgrade, new nodes or a small patch to fix a vulnerability.
Part of the upgrade may require you having a functional system. In this case, our licensing allows for some time in between testing the new system with the upgraded version and allowing the system to run with the current version.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Client Release 1.5.65
Wed 14 February 2018 | general release client
We have released SFTPPlus Client version 1.5.65 which fixes a defect for recursive uploads over SFTP from a Windows client to a Linux server.
Announcing the SFTPPlus and Docker repository
Wed 31 January 2018 | blog
Docker containers have been a constant presence in the worlds of DevOps and cloud computing. We have recognized this only through a passing mention in our product page that SFTPPlus can run in a Docker container.
However, we have not gone beyond that, until now.
We are pleased to announce the creation and release of a dedicated, public, MIT-licensed repository to make the creation and running of Dockerfiles more accessible. Whether you are already a customer of ours, currently evaluating SFTPPlus or you are interested in seeing a managed file transfer service run in Docker. Simply head over to our repo, clone, and follow the instructions to run an SFTPPlus instance in Docker.
SFTPPlus running in a Docker container does not lose functionality and makes full use of the infrastructure provided by a Docker container. You can audit and archive SFTPPlus server events (also knows as logs) using the default Docker log driver.
Once you have set up the SFTPPlus Dockerfile, what's next? Why not use Docker Compose to run multi-container Docker applications.
You can use Compose to create the following specialized instances like:
- SFTPPlus instance - Handle file transfers over SFTP / FTPS / WebDAV. Data storage is backed by a volume.
- Authentication and Authorization instance - Respond to authentication and authorization requests over HTTP. You can use this instance to authenticate other services inside your deployment.
- Audit instance - Receive, over HTTP, events and logs generated by SFTPPlus. Use this instance to process logs and events from other services.
- File Processor instance - Receives events over HTTP in order to further process them based on the rules specified by your business logic.
See our Github and documentation
You can view the scripts and instructions to get started quickly in our GitHub repository.
A users guide is available in our Docker documentation page.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Release 3.30.0
Thu 25 January 2018 | general release
We are pleased to announce the latest release of SFTPPlus version 3.30.0.
New Features
- It is now possible to dynamically dispatch files to different destinations based on the name of the file which was dispatched. [#4555]
- The HTTP authentication method can now send requests which are authenticated using the HTTP Basic authentication (BA) method. [#4589-1]
- The HTTP event handler can now send requests which are authenticated using the HTTP Basic authentication (BA) method. [#4589]
- The file-dispatcher event handler now has the capability to delete files. [client-side] [#4624]
- You can now configure an account to amend the requested file for an upload by prefixing it with a universally unique identifier (UUID4). This option is available for the SFTP and SCP protocols. [server-side][sftp][scp] [#4643]
Deprecations and Removals
- The ${SHAREPOINT_CA} and ${SHAREPOINT_CRL} placeholders were replaced by the more inclusive ${MICROSOFT_IT_CA} and ${MICROSOFT_IT_CRL}. The ${SHAREPOINT_CA} and ${SHAREPOINT_CRL} placeholders will continue to be available as an alias for Microsoft IT CA. [#4625]
You can check the full release notes.
Introducing SFTPPlus to high availability and resiliency
Tue 23 January 2018 | article infrastructure
Where does SFTPPlus sit in your IT infrastructure
The SFTPPlus software stands at the OSI Layer 7 or the TCP Layer 4. In order to have a fully fault tolerant system, you need to implement resilience at all the other layers including the OS. SFTPPlus can be integrated with external tools in order to meet the requirements for a fault tolerant infrastructure.
For those not familiar with OSI and TCP please read on.
SFTPPlus on the OSI
The OSI model is a model that characterizes and standardizes communication functions. The layers range from layer 1 right through to layer 7. In the OSI, or Open Systems Interconnection model, SFTPPlus sits in the OSI Layer 7 or on the application layer.
The application layer sits at the top of the OSI model and is the software, hence the name application, layer between the end-user and the networking layers underneath.
In order to have a fault tolerant system, SFTPPlus on the upper layer 7 will need to be integrated with the bottom layers.
SFTPPlus on the TCP
In addition to the OSI model, another way of understanding where SFTPPlus plays a role in your infrastructure is via the TCP layer. SFTPPlus sits in the TCP Layer 4 or the application layer. This is the topmost layer which defines the TCP/IP application protocols and how SFTPPlus interfaces with the Transport layer, the layer below the application layer, and other services that use the network.
Installing SFTPPlus in high availability and resilient environments
The following are introductory information for this topic.
About high availability
High availability means creating a system that is always available for use. It could be a percentage of 99.99% uptime guaranteed. In this case, you will be looking at a downtime of merely five minutes of time over the course of the year.
There are extra items that one can add to ensure that this system is available at the guaranteed uptime rate. In this case, one can look into active-active or active-passive scenarios. To build a system that is highly available means that there may be an additional cost associated with ensuring this.
About resilience
The following can be deduced as a definition of a resilient control system:
"A resilient control system is one that maintains state awareness and an accepted level of operational normalcy in response to disturbances, including threats of an unexpected and malicious nature"
High availability and resilience tend to be used interchangeably. However, having a highly available system does not necessarily mean that all required functions are still in use and available. This is where having a resilient system come into action. Even if a system has high availability, can it still function to a required level of standard, operational normalcy? You will still wish to utilize a system with the same users, storage and database as found in the usual system.
About fault tolerance
On the event of failure, the system remains available in order to maintain the high uptime. There may be a performance break or slow down but the services are still available.
You may add additional devices or protocols for a fault tolerant system - RAID set up, multiple network paths for fault tolerance (on the event of a failed network path) and load balancers are such examples.
About clustering
Clustering involves creating a cluster of two or more nodes or members that work together in order to perform an action. They can be grouped in the following major types; storage, high availability, load balancing and high performance clusters.
The main clusters that relates to SFTPPlus in a given system are high availability and load balancing types of clusters.
High availability clusters involve the provision of highly available services by ensuring that any single points of failure are eliminated. This is done by failing over services from one cluster node to another should that node be no longer in operation. This ensures the ability to maintain data integrity.
Load balancing clusters sends off network requests to a number of cluster nodes in order to balance the request load among the cluster nodes. This ensures scalability of a network since administrators can match the number of nodes according to load requirements through load balancing algorithms.
How can SFTPPlus be integrated in these environments
Active-Active and Active-Passive Scenarios
Active-active and Active-passive are two types of cluster configurations in a high availability scenario.
The details between these two scenarios are laid out below from Sybase.
Active-Passive configurations
Setup: A single Adaptive Server runs either on the primary node or on the secondary node. The Adaptive Server runs on the primary node before a fail over and the secondary node after fail over.
Failover: When a system fails over, the Adaptive Server and its associated resources are relocated to, and restarted on, the secondary node.
Failback: Failback is a planned fail over or relocation of the Adaptive Server and its resources to the primary node. Failback is not required, but can be done for administrative purposes.
Client Connection failover: During failover and failback, clients connect to the same Adaptive Server to resubmit uncommitted transactions. Clients with the failover property reestablish their connections automatically.
How to set up SFTPPlus in active-passive scenarios
In this infrastructure scenario, the second system is offline and only commences when the main SFTPPlus system is down.
Since the server.ini configuration is stored in a single file, you can create a file copy task to keep the system configurations in sync. Make sure to also transfer additional files that are required - such as SSH keys, and SSL keys and certificates - to ensure a smooth transition. When it is time to use the secondary system, the SFTPPlus instance will then read the latest server.ini configuration file.
Active-Active configurations
Setup: Two Adaptive Servers are configured as companion servers, each with independent workloads. These companions run on the primary and secondary nodes, respectively, as individual servers until one fails over.
Failover: When fail over occurs, the secondary companion takes over the devices, client connections, and so on from the primary companion. The secondary companion services the failed-over clients, as well as any new clients, until the primary companion fails back and resumes its activities.
Failback: Failback is a planned event during which the primary companion takes back its devices and client connections from the secondary companion to resume its services.
Client Connection failover: During failover, clients connect to the secondary companion to resubmit their uncommitted transactions. During failback, clients connect to the primary companion to resubmit their transactions. Clients with the failover property reestablish their connections automatically.
How to set up SFTPPlus in active-active scenarios
In this infrastructure scenario, both SFTPPlus systems are receiving and processing requests. If one system goes down, the other will handle all the requests.
To implement SFTPPlus in this scenario, a simple file copy will not work. This is because running SFTPPlus instances will not check changes in the local file configuration (server.ini) in order to reconfigure. In addition, there are other files that are also required - such as all SSH keys in use and other related files, all SSL certificates required, any logs that need to be kept for auditing purposes, any externally referenced scripts used in pre- and post- transfer processing, and so on.
One method of achieving an active/active implementation is to manually set up the 2 nodes to rely on a single external authentication method (HTTP or LDAP). In this way, accounts are managed in the single external system, and those accounts will be automatically available for both SFTPPlus instances.
Installing SFTPPlus for disaster recovery
Disaster recovery is part of business continuity plans (or business continuity and resiliency plans) which is the process of creating systems of prevention and recovery to deal with potential threats to a company. The use of the term “recovery” has also been used when talking about resiliency.
Providing that the server configuration and related configuration files are properly maintained and backed-up, you can integrate SFTPPlus as part of your disaster recovery plans.
Conclusion and next steps
The application of these does not immediately guarantee results in achieving high availability or resiliency. Please consider these guides merely as a layer within multiple others when implementing a high available, resilient and secure managed file transfer solution.
Since features are constantly changed, we did not touch on any specifics within SFTPPlus. Please consult our documentation for the configuration and operations information, as well as practical users guides.
This resource is written as of SFTPPlus version 3.29.0.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
Choosing the best protocols for securing data and file transfers
Mon 22 January 2018 | article security
Why read this guide
In order to implement a secure managed file transfer system, you will need a good understanding of the supported services and protocols involved.
This article provides an overview of the supported protocols, including the advantages and disadvantages of these protocols as well as situations for the use of these services.
The first part focuses on protocols that we recommend you reconsider in using and the rest of the article is followed by services that we do recommend.
Protocols to reconsider when securing data and file transfers
The following, FTP and HTTP, are covered below as they both pose two services that offer the least advantage in terms of securing data and file transfers.
File Transfer Protocol (FTP)
Shortform for File Transfer Protocol, the objectives of FTP are 1) to promote sharing of files (computer programs and/or data), 2) to encourage indirect or implicit (via programs) use of remote computers, 3) to shield a user from variations in file storage systems among hosts, and 4) to transfer data reliably and efficiently.
FTP has had a long evolution over many years starting with its beginnings published as RFC 114 on 16 April 1971. Over time there has been other forms of file transfer protocols made available as there had been vulnerabilities and weaknesses with FTP such as:
- Brute force attacks which is attacking via computing credential combinations.
- FTP bounce attacks which is an exploit enabling an attacker to use the PORT command to request access to ports indirectly through the use of the target machine as a man in the middle request.
- Packet capture through the use of packet capture tools.
- Port stealing where traffic directed at a port is stolen or intercepted by an attacker.
- Spoofing attack where the attacker may use a tool to try multiple instances of an IP address in order to assume the correct, and therefore spoofing, the host address of the target machine.
- Username enumeration is part of the discovery, or enumeration, process prior to an attack of a network or service by obtaining usernames associated with the service.
There are also limitations to the protocol. For example, there is no ability to encrypt data on transit. Data in transit can be sniffed using freely available tools since the transmissions of usernames, passwords, commands and other data is not encrypted. An attacker can run a packet sniffer over the network can sniff out FTP credentials. In addition, there is no integrity checking of files to ensure that data integrity remains since this is not included as a feature of the protocol.
Situations to use the FTP service:
There is a chance that your initial file transfer system may even be in FTP, depending on the age of the system. However, FTP has many security weaknesses and vulnerabilities as mentioned previously.
Those wishing to continue to use FTP and to do so in a secure manner may find themselves integrating other software to ensure security, creating additional scripts or taking on board additional maintenance. For example, there is no built-in integrity check however scripting work can be done to create a checksum integrity checking process and added at the end of a file transfer. There is also further additional overhead in ensuring that FTP remains secure such as integration with other applications for additional layers of security.
The FTP service is accessible by enabling the service and then configuring the address, port, passive port range, passive address, idle data connection timeout and more.
Hypertext Transfer Protocol (HTTP)
HTTP, shortform for Hypertext Transfer Protocol, is an application-level protocol for distributed, collaborative, hypermedia information systems. It is a generic, stateless, protocol which can be used for many tasks.
HTTP, in use by the World-Wide Web global initiative since 1990, is a protocol used in many tasks related to common usage of the web such as browsing websites. This is relevant to SFTPPlus since we offer a browser-based file management utility.
Without SSL/TLS, there is no way to encrypt data in transit. Other downsides to HTTP, in the context of SFTPPlus, include:
- Packet capture through the use of packet capture tools.
- Man-in-the-middle attack where the attacker intercepts and relays false malicious content between two parties.
- Credentials are sent in a plain text encoding when using the SFTPPlus HTTP Basic Auth API.
Situations to use the HTTP service:
HTTP may be used internally within a highly secured network where there are already mechanisms in place to protect the environment.
We offer HTTP based micro-services and endpoints as part of our public API. In this case, the API is used in conjunction with other security mechanisms in place for the environment.
The HTTP service is accessible by enabling the service and then configuring the address, port, idle connection timeout and maximum concurrent connections.
Protocols to consider when securing data and file transfers
The following are protocols and services that we do recommend for securing data and file transfers. This is not an exhaustive list.
Implicit FTPS or FTPS Implicit SSL (FTPIS)
FTPIS, or implicit FTPS, is the use of the FTP protocol where secure data transfer is invoked via SSL as soon as the connection starts or after the OK reply is sent by the server. In implicit mode, an FTPS client is expected to “immediately expected to challenge the FTPS server with a TLS ClientHello message. If such a message is not received by the FTPS server, the server should drop the connection.” This means that the use of SSL is implied. This is illustrated in the diagram above.
The advantage is that this service is safer than the use of the FTP protocol due to implementing SSL meaning that data transmission is encrypted.
Situations to use the FTPIS service:
Use FTPIS when you wish to use a more secure FTP for file transfer and where SSL does not need to be invoked prior to login. However, if possible, use FTPES as described further below.
Explicit FTPS or FTPS with Explicit SSL (FTPES)
In explicit mode, an FTPS client must “explicitly request” security from an FTPS server and then step up to a mutually agreed encryption method. If a client does not request security, the FTPS server can either allow the client to continue in insecure mode or refuse the connection.
The advantage is that this service is safer than the use of the FTP protocol due to implementing SSL. Prior to user connection, both the server and client must negotiate the level of security used.
Situations to use the FTPES service:
Use FTPES when you wish to use a more secure FTP for file transfer and where SSL needs to be invoked prior to login. However it should be noted that this not ensure that each and every session and data transfer is secure. FTPES is only a tool allowing the client/server to negotiate the accepted level of security with each session.
Notes for both FTPES and FTPIS
Since both are FTPS (FTP over TLS/SSL), they share some common advantages as listed, non-exhaustively, below:
- The advantages afforded by SSL is used - certificate authorities, certification revocation lists, transmission encryption and more.
- Certain regulations and compliance obligations may require data transmissions to be encrypted but it should be noted the difference between FTPES and FTPIS when it comes to which stage the encryption occurs.
- The protocols make use of TLS (Transport Layer Security) encryption. It should be noted that in SFTPPlus, the TLS version can be used
SSH File Transfer Protocol or Secure File Transfer Protocol (SFTP)
SFTP is a network protocol that allows for file access, transfer and management capabilities over the SSH (Secure Shell) protocol channel.
The advantages for SFTP include:
- Designed to be used to implement a secure remote file system service and also a secure file transfer service.
- Runs over a secure channel, SSH, so that the server has already authenticated the client. The identity of the client user should also be available to the protocol.
- Data is encrypted based on a configured cipher list agreed upon by the server and client.
- There is the option to implement user access via SSH keys only or via a combination of password and SSH keys. If authenticating via SSH keys, the client does not need to go through password recollection so long as the SSH key is correctly configured on the server.
- Certain regulations and compliance obligations may require data transmissions to be encrypted.
The SFTP protocol follows a simple request-response model where each request and response contains a sequence number and multiple requests may be pending simultaneously.
Situations to use the SFTP service:
The protocol assumes that both ends of the connection have been authenticated and that the connection has privacy and integrity features already in place and that security issues are left to the underlying transport protocol.
Since the protocol provides file system management feature, the server must have the correct access controls in place and implement correct authorization and enforce access controls.
In this case, when you implement SFTP ensure that you are doing so within an AAA (authorization, authentication, auditing/accounting) security design framework on SFTPPlus.
HTTP over SSL/TLS (HTTPS)
HTTPS, shortform for HTTP over TLS, provides security measures in using HTTP via SSL and its successor, TLS.
The HTTP protocol is further secured via SSL and its successor, TLS (Transmission Layer Security), thus this is referred to as HTTPS. HTTPS provides end-to-end security for browser-based applications.
Other advantages to using HTTPS:
- TLS can harden TCP against Man-in-the-middle attacks where clients and servers exchange certificates which are issued and verified by a trusted third party called a certificate authority (CA).
- HTTP Public Key Pinning (HPKP) allows HTTPS website to overcome impersonation via the use of fraudulent certificates.
- Certain regulations and compliance obligations may require data transmissions to be encrypted
Situations to use the HTTPS service:
Since the SFTPPlus file management utility is accessible via the web browser, the HTTPS service is a more secure alternative compared to HTTP.
HTTPS is a must especially when the resource is going to be public (Internet) facing.
The HTTPS service is accessible by enabling the service and then configuring the SSL/TLS options such as the SSL cipher list, allowed SSL/TLS methods, SSL certificate, SSL key, certificate authority, certification revocation list and more.
Conclusion and next steps
The application of one protocol over the other does not immediately guarantee security. Please consider these services merely as a layer within multiple others when implementing a secure managed file transfer solution.
Since features are constantly changed, we did not touch on any specifics within SFTPPlus. Please consult our documentation for the configuration and operations information, as well as practical users guides.
This resource is written as of SFTPPlus version 3.29.0.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
Securing data and file transfers between SFTPPlus and third parties
Sun 21 January 2018 | article security
Why read this article
In order to have a fully established file transfer and sharing system, you need to implement integration at all the other layers including the OS. SFTPPlus can be integrated with external tools and third parties in order to help establish these integration requirements.
This article is written for those new to SFTPPlus and those involved in the business function of securing file transfer software. Topics are covered for various levels of knowledge to reach a wider audience.
Where does SFTPPlus sit in your IT infrastructure
The SFTPPlus software stands at the OSI Layer 7 or the TCP Layer 4. SFTPPlus can be integrated with external tools in order to secure data and file transfer with third parties.
For those not familiar with OSI and TCP please read on.
SFTPPlus on the OSI
The OSI model is a model that characterizes and standardizes communication functions. The layers range from layer 1 right through to layer 7. In the OSI, or Open Systems Interconnection model, SFTPPlus sits in the OSI Layer 7 or on the application layer.
The application layer sits at the top of the OSI model and is the software, hence the name application, layer between the end-user and the networking layers underneath.
SFTPPlus on the TCP
In addition to the OSI model, another way of understand where SFTPPlus plays a role in your infrastructure is via the TCP layer. SFTPPlus sits in the TCP Layer 4 or the application layer. This is the topmost layer which defines the TCP/IP application protocols and how SFTPPlus interfaces with the Transport layer, the layer below the application layer, services to use the network.
While the above information only provides a brief introduction, this should help you understand how SFTPPlus integrates with the networking components (the file transfer protocols) as well as the components on the application level (other systems).
Introduction to file transfer protocols supported by SFTPPlus
For those making the leap to a managed file transfer service for the first time, they may also be thinking about networking components such as which file transfer protocols to support. If your company is currently using FTP, then you may want to switch to FTPES or FTPIS for better security. Or perhaps SFTP for features such as the security of key exchanges.
File transfers are secured via the support of file transfer protocols such as SFTP, FTPS, FTPS, and HTPS. For those that are not familiar, please read the overview of the supported protocols from our Quick Start section in our documentation.
Logging and monitoring network operations with SFTPPlus
Introduction
When you create file transfer systems that interact with services, protocols, databases, users and data, it is important to ensure that the system is being protected and monitored from unauthorized modifications, use, access or destruction.
Ensuring that activities are under proper monitoring and logging is also an important aspect of secure file transfer infrastructures. Should there be access attempts from that particular IP range? Should this file transfer service port be in use at all? Are there subsets of data that are critical enough that an alert mechanism be put in place for failed transfers in that source? The answers to questions like these will help provide the basis for meeting logging and auditing requirements for your infrastructure through our audit and logging mechanisms.
Databases
SFTPPlus can be integrated with external database and logging tools such as SQLite, MySQL, Syslog, Windows Event Log.
These integrations will help in any logging, reporting and auditing obligations as is the case for organizations seeking to meet compliance with bodies such as GDPR, HIPAA, GPG13 and more.
SFTPPlus will keep a detailed log of any file which is transferred and can include details about the initial transfer request and the status of the request finalization, logs status changes to device and configurations, login attempts, connection attempts to and from the server or client, session activities and more.
Email resources for email alerts
Users can set up vital email alerts to monitor for any specific server events.
By creating a new email resource, SFTPPlus formulates outgoing emails as though they were coming from an email client.
Access to an SMTP server is necessary. You may use any email service available on your network (public or private). You may use anonymous SMTP, or a preexisting account on that server/service. A local or private SMTP server may also be used.
Once the email resource and Event Handler are configured, the body of any email sent will consist of a JSON object for the event that triggered the email. The recipient(s) and subject line of the email are configurable items.
Integrating SFTPPlus with third parties via the API
SFTPPlus provides public APIs which extend the identity management, file access, audit functionality and more of the SFTPPlus MFT Server using HTTP based micro-services / endpoints. The HTTP APIs can be used to integrate file transfer processes with disparate systems, such as web applications, that need to interface with SFTPPlus.
While it is targeted to HTTP, the HTTP API is used by integrator only as a layer of operations underneath secured networks such as having the services only available under corporate VPNs or proxies.
For more details about the API, please consult our developer section in the documentation.
Potential use case for HTTP Authorization
A potential use case for the API is utilizing the HTTP Authorization for SFTPPlus. This is deployed in a DMZ where certificate-based authentication cannot be used, only a username/password authentication with a time limit expiration.
Case study with load balancers and HTTPS push from third party via SFTPPlus API
This case study involves integrating with a third party. In this case, the third party is a web application functioning as the client.
Through the HTTPS service that is available with SFTPPlus, the third party developer works with the SFTPPlus HTTP API to authenticate the users and to allow them to upload content (push) to the SFTP servers.
Subsequently the corporate, or internal network, are authenticating via the SSH key exchange (as one of the possible methods) and pulling content from the servers.
While the topic is covered in another article, the servers are also set up for high availability and resilient environment via a load balancer. In this case, the load balancer is utilizing the weighted round-robin algorithm depending on the server ‘weight’.
Ensuring high availability is also a pathway to secure file transfer operations by making sure that critical data is constantly available. Load balancers can be used with SFTPPlus to set up high availability.
Through a combination of choosing secure file transfer protocols, smart use of the SFTPPlus API and structuring file transfer operations to function in a high availability environment, you can further secure your data and file transfers with your company.
Integrating SFTPPlus with DMZ and buffer zones
A DMZ (or demilitarized zone) is implemented in order to separate servers and other resources from the external or public-facing facing Internet and their internal, trusted networks will run through a number of different configuration options. The standard example used is two firewalls, one firewall for the external or public facing resources and the other for the internal resources, serving a subnetwork.
Case study with DMZ and buffer zones
For a case study on how SFTPPlus is integrated with a DMZ, see above for an example of an internal company user transferring files towards external, public-facing servers.
In this case, the FTP/SFTP ‘Inbox’ folder which resides within the DMZ will utilize the SFTPPlus file-dispatcher Event Handler to dispatch files to the ‘Outbox’ folder within the DMZ.
The file-dispatcher event handler has been configured to move files from the SFTPPlus Inbox folder to the SFTPPlus Outbox folder based on a matching expression - either global or regular expression. In this instance, we can say that the matching expression is for all PDF files. All of this happens with the DMZ which acts as a buffer zone between the media PC in an internal network to external servers.
From the SFTPPlus Outbox folder, which serves as a cache of matched files, users can initiate a client transfer to the external public facing servers outsize the DMZ.
Implementing AAA (Authentication, Authorization and Accounting) frameworks
SFTPPlus allows for an AAA system to be implemented. AAA refers to Authentication, Authorization and Accounting. It is a system to mediate and manage network access based on the process of identifying a user (authentication), granting or denying access to the user (authorization) and keeping track of the user’s activities on the network resource (accounting).
Accounting part of the AAA framework
As SFTPPlus operates, it will emit a set of events which contains a unique ID and defines a specific operation carried out by the server. A common action for an event is to send it to one of the supported logging systems. This covers the Accounting requirement of the AAA (Authentication, Authorization, and Accounting) security design framework.
Utilizing an accounting, also seen as auditing, framework is a way to ensure that any compliance or logging obligations and requirements are met.
Authorization part of the AAA framework
The use of authorization is one of the fundamental aspects of network and resource management security. By building an authorization framework, you can ensure that users have correct access to network resources.
In the above diagram, we have two users in the same department or user group but both of these users have different access requirements. After authentication via the authentication server, how does an administrator ensure that the correct authentication framework is applied? One user can only have read-only rights to shared folder and full-control for a common home folder. Whereas another user has full-control-allowed access to both the common folder and all other folders underneath, including a shared folder with the first user.
In the above diagram, the permissions framework can be set up on a global or on a per-path basis, including fine-grain details such as permissions for matching expressions.
Even after a user group is authenticated and the correct users are in their respective accounts, a solid authorization framework will ensure that any additional user access rights policies are applied.
Authentication part of the AAA framework
The server-side security of SFTPPlus is designed based on the Authentication, Authorization and Accounting (AAA) components. Authentication can be integrated with external third parties - Windows Domain Accounts - or with external resources such as via the domain controller, via the SSH RSA/DSA keys or SSL certificates.
When compiling how you will secure your system, it is important to take stock of how you are mediating and managing network access based on meeting authentication, authorization and accounting requirements.
Integrating SFTPPlus with post-processing actions
SFTPPlus can function suitably when anti-virus applications are installed to protect the environment on the machine. This integration is done as part of the transfer configuration for post-processing actions.
Most anti-virus applications have a real-time protection component that will scan files on creation, when accessed, and on execution. These operations will not affect the overall performance of the system.
Case Study - Virtual machines
To further secure data and file transfers, users can create two installations running in active / passive mode behind a load balancer. These two instances will share the same users, database and storage.
Running in AWS, a new instance is created when one dies to maintain high availability.
SFTPPlus can be integrated with a third party virtual private cloud, as well as load balancers to ensure high availability and resiliency.
Conclusion and next steps
The application of these does not immediately guarantee security. Please consider these guides merely as a layer within multiple others when implementing a secure managed file transfer solution.
Since features are constantly changed, we did not touch on any specifics within SFTPPlus. Please consult our documentation for the configuration and operations information, as well as practical users guides.
This resource is written as of SFTPPlus version 3.29.0.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Release 3.29.0
Thu 11 January 2018 | general release
We are pleased to announce the latest release of SFTPPlus version 3.29.0.
New Features
- An event with ID 30079 is now emitted when an SFTP location sends a banner message during authentication. [#4293]
- The HTTP file transfer service now supports the HEAD method for folders which return OK when the folder exists. [#4493]
- The HTTP event handler now sends the local timestamp for the generated event. Previously, the event was sent without a timestamp and the event timestamp was supposed to be created by the PHP WebAdmin. To take advantage of this change, you will need PHP WebAdmin version 1.9.0 or newer. [#4577]
Defect Fixes
- An error is no longer produced when the source location for a SFTP transfer is a Bitvise SSH server. [#4297]
- An internal server error is no longer produced by the HTTP file transfer service when a file or a folder is accessed with an unsupported method. [server-side][http] [#4493]
- The HTTP event handler now sends the IP and PORT of the remote peer associated with the event. Previously, this detail was omitted and PHP WebAdmin was using the address of the SFTPPlus server instead of the client connected to the server. [#4577]
- The limit of pending files to be transferred for a single transfer was raised from 5 000 files to 100 000 files. [client-side] [#4586]
You can check the full release notes.
SFTPPlus MFT Trial Releases Now Available
Thu 11 January 2018 | general release
It is now easier for all enterprises - large and small - to evaluate SFTPPlus MFT with the release of a trial version which includes full functionality of the software suite.
Customers seeking a trial have the choice of either the MFT Server, MFT Client or both for major operating systems on Windows and Linux.
SFTPPlus MFT is a software suite for managed file transfer (MFT) with Client and Server that may be licensed and used as standalone modules or together as a MFT solution.
Whether you need file transfer protocols support for FTPS, SFTP, HTTPS or WebDAV, we have you covered.
How do I obtain a trial version?
Email us at sales@proatria.com to start your evaluation version today.
Once you have your trial, make sure to view and bookmark our 5 minute quick guide.
How long does the trial version last?
Trial versions last for 30 days after a major release. For example, if version 3.xx.x was released on 01/01/2018 then the trial version will last until 01/31/2018.
What happens to my configuration data if I want to switch to the full version?
You can maintain your server configuration data simply by copying the configuration file over the configuration file in the full version.
As for SSH keys, SSL certificates and other items initialized by yourself or SFTPPlus, you can also use these providing that the locations remain the same as what is already in the configuration file during the evaluation period.
Further instructions to upgrade to the full version are found in our documentation.
Who do I contact for technical and other support?
Since we offer support as part of the evaluation package, you can email the Support team at support@proatria.com.
About SFTPPlus MFT
SFTPPlus MFT is a managed file transfer software product that supports FTP, Explicit FTPS, Implicit FTPS, SFTP, SCP, HTTP and HTTPS.
SFTPPlus MFT can be installed either as an on-premise solution supported on Windows, Linux, AIX, OS X, Solaris, FreeBSD, HP-UX or on the cloud as Docker containers or AWS instances.
Security, correctness, functionality and performance as well as integration support and no vendor lock-in are key requirements of SFTPPlus MFT.
Our worldwide customer profile includes government agencies and businesses large and small across Europe, USA, Middle East, Asia, Australia and Far East. Pro:Atria also works with integrators and system design teams including IBM, DXC, Fujitsu, Capita and Tata (amongst others). Customers are from all sectors including retail, financial, manufacturing, healthcare, education and transport as well as government agencies and departments.
This article was written as of SFTPPlus version 3.28.0.