Articles from infrastructure category
IPv6 support for HTTP/S, FTP/S, SFTP and SCP File Transfer Services
Mon 04 June 2018 | article infrastructure
Why get ready for IPv6?
According to the Akamai Q1 2017 State of the Internet Connectivity Report, "approximately 5 million IPv4 addresses were depleted from available pools at the Regional Internet Registries in the first quarter, leaving approximately 39 million addresses remaining."
In response to the steady depletion of IPv4 addresses, we see greater adoption of many large mobile and broadband networks actively rolling out IPv6 connectivity. According to World IPv6 Launch, among the top 10 participating networks with more than half IPv6 deployment rates include Comcast, ATT, Verizon Wireless and Deutsche Telekom AG.
Now is a good time to brush up on your knowledge of deploying IPv6 in your organization. For those with a lack of knowledge or training in IPv6 implementation, there is an even greater urgency when addressing the potential security impact of the rollout in the organization. Such scenarios are amplified when administrators do not have the required level if minimal expertise in IPv6 to ensure there is protection against threats. If you are in the front-line of IPv6 deployment and file transfers in your own organization, you will find this post of useful interest.
A brief introduction to IPv6
IPv6 was first introduced by IETF in 1998, via RFC 2460, which has since been updated via RFC 8200 published in July 2017. This is the new version of the Internet Protocol and a successor to IPv4.
The main updates are as follows:
Expanded addressing capabilities
This involves increasing the IP address size from 32 bits to 128 bits. This allows greater support in addressing hierarchy, more addressable notes, scalability of multicasting, and addition of anycast address.
Simplified header formats
This involved dropping or making optional some of the IPv4 header fields.
Improved support for extensions and options
The way IP header options are encoded allows for more efficient forwarding and greater flexibility for new options.
Flow labeling capability
This allows sender requests to be treated in the network as a single flow.
Authentication and privacy capabilities
Extensions are added in order to support authentication, data integrity, data confidentiality.
While it has been some length of time since the first introduction, each day brings forward the pressing need to implement IPv6 as IPv4 addresses become exhausted. Greater adoption for IPv6 by vendors, including increase in knowledge and support, means that deployment is now more feasible for administrators than ever before.
IPv6 and SFTPPlus
Enabling IPv6 on SFTPPlus for HTTP/S, FTP/S, SFTP and SCP
SFTPPlus supports configuring IPv6 addresses for the HTTP, HTTPS, FTPS, FTP, SFTP and SCP file transfer services.
We have written a starter guide with details on how you can enable IPv6 with SFTPPlus. Please to go to the documentation section on IPv6 support.
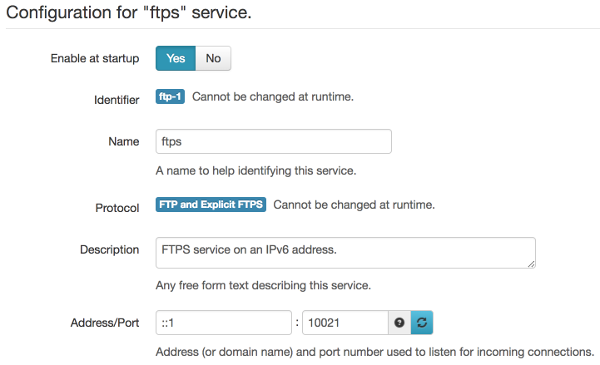
When configuring a new service on SFTPPlus, an IPv6 address can be used. To accept connections on all available IPv6 interfaces, simply use the :: address like the simplified test configuration below:
[services/ftps] enabled: Yes name: FTPS Service on an IPv6 address. address: ::1 port: 10021
Please consult the configuration documentation for more details about each type of file transfer service.
Enabling IPv6 on SFTPPlus Local Manager
Similar to enabling IPv6 on file transfer services, you can set the SFTPPlus Local Manager to listen in on an IPv6 address via the same address field as the services.
Administrators can add this via the SFTPPlus Local Manager Services section:
Enabling authentication methods with IPv6
We support IPv6 address when authentication file transfer accounts via the ldap authentication method and via the HTTP API authentication method.
IPv6 implementation and security considerations
The following are some considerations in implementing IPv6 securely.
Conduct an inventory audit
Tag which file transfer scenarios (server, client, protocol) require IPv6 implementation and support.
Communicate with your vendors
Notify your vendors as to what level of support is provided for IPv6. If not supported, inquire if there will be plans on the product roadmap for the support.
We have added IPv6 support for file transfer services, as of SFTPPlus version 3.33.0, in response to customer needs to roll out such support.
Conduct a security-focused audit on IPv6 deployment
Both IPv4 and IPv6 share similar properties when it comes to security. In this case, take an audit of which of these properties can be carried over within an IPv6 deployment.
Last but not least - do not overlook security risks and requirements for IPv6
Network administrators overlooking the effects of IPv6 in their network will face security risks. IPv6 packets is susceptible to attacks like MITM (Man-in-the-Middle) attacks. Bad actors may also attempt to eavesdrop by making use of upper-layer protocols such as TLS (Transport Layer Security) or SSH (Secure Shell). Another potential security threat is bypassing IPv4-only firewalls and ACLs using functional IPv6 tunneling protocols as described in the Carnegie Mellon University CERT/CC blog post here.
IPv6 troubleshooting
The following are introductory advice for those troubleshooting IPv6 within a file transfer scenario.
- Ensure that the protocols to be used are fully tested with SFTPPlus.
- Ensure that FTP proxies, firewalls and other layer 7 technologies properly support IPv6.
- Ensure that any other boundary facing technologies are implementing IPv6 correctly.
It is also good to keep note of future changes to the protocol. For example, design changes to the new IPv6 extension header could mean security implications based on how the new changes work with existing extension headers.
Those evaluating SFTPPlus and customers with a valid support contract can leverage help from the SFTPPlus Support team for queries in regards to SFTPPlus and IPv6 deployment.
Other resources
- World IPv6 Launch
- SANS Institute InfoSec Reading Room guide on IPv6 Attack and Defense
- IETF specification on IPv6 on RFC 8200
- List of IPv6 RFCs and Standards Working Groups
- Infosec Today on basic IPv6 Security Considerations
- Internet Society IPv6 Case Studies
This resource is written as of SFTPPlus version 3.34.0.
The details in this resource is for guidance only. Influences such as own security policies, requirements, and threat models should be considered when adopting this type of guidance.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
Data Loss Prevention - Systems, Software and Strategies
Thu 19 April 2018 | article infrastructure
What is Data Loss Prevention (DLP)?
Data Loss Prevention (or DLP for short) is the application of technology and policies in order to detect and prevent potential data breaches and data ex-filtration. Data that is of particular interest include sensitive emails, documents and other information leaving the organizational boundary. Data Loss Prevention is one out of many options used in today's arsenal of defense against threats and attacks, and also a layer to harden overall data security.
While SANS may write that DLP is primarily concerned with identifying sensitive data, we have taken on board a more holistic look beyond identification.
Data loss prevention can be in the form of the following:
- Network-based DLP.
- Endpoint DLP which monitors on the application level such as email client used.
- Network policies enforced for information leaving the network.
- UI, for example in the form of pop up tips, that will help reinforce data protection awareness training.
- Common dictionaries and regular expressions syntax used to create content protections rules.
- Staff awareness training.
- Using file tagging to secure data that can contain intellectual property or trade secrets.
The above is not an exhaustive list.
Data loss prevention tend to be interchanged with data leak prevention when the situation involves the lost data being acquired by an unauthorized third party. However for this article, we will also include both data loss and data leak scenarios under the overall DLP umbrella term.
Upon application of DLP, you can ensure compliance with regulations governing use of data and ensure obligations for best practices are being met. These compliance and regulations include Health Insurance Portability and Accountability Act (HIPAA), (Payment Card Industry) PCI compliance, and General Data Protection Regulation (GDPR) to name a few.
Data loss prevention in file transfers
Within the territory of file transfer, data loss happens via information being inadvertently or intentionally sent to an unauthorized individual through the use of either file transfer software or file transfer protocols. It can also happen due to human ignorance or negligence - for example, uploading sensitive documents using an unapproved cloud provider.
Imagine a scenario where an employee in a large company has just transferred a series of files containing confidential data. Or another scenario where a small business owner has data residing on USB (unencrypted) and has since been lost.
It is with these two scenarios where we see data loss prevention not being applied for both data in transit (the transfer of files containing confidential information) and data at rest (the files residing within the USB).
Types of data in file transfers
As an introduction, the following paragraphs (from Wikipedia) summarizes the differences between data at-rest, data in-use and date in-motion.
Data at-rest
"Data at rest" specifically refers to old archived information. This information is of great concern to businesses and government institutions simply because the longer data is left unused in storage, the more likely it might be retrieved by unauthorized individuals. Protecting such data involves methods such as access control, data encryption and data retention policies.
Data in-use
"Data in use" refers to data that the user is currently interacting with. DLP systems that protect data in-use may monitor and flag unauthorized activities. These activities include screen-capture, copy/paste, print and fax operations involving sensitive data. It can be intentional or unintentional attempts to transmit sensitive data over communication channels.
Data in-motion
"Data in motion" is data that is traversing through a network to an endpoint destination. Networks can be internal or external. DLP systems that protect data in-motion monitor sensitive data traveling across a network through various communication channels.
Data Loss Prevention and SFTPPlus MFT
DLP monitoring network activity
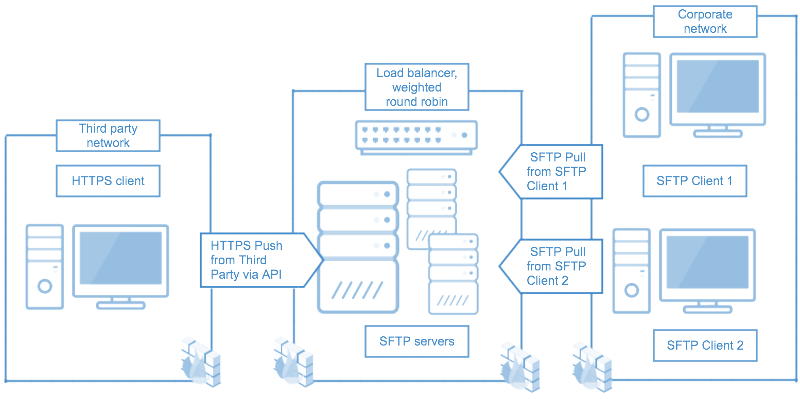
The DLP software is integrated into the network using a network TAP (terminal access point) port to perform real-time scanning and analysis of network traffic.
In addition to DLP inspection for data in-transit, DLP inspection can also be applied for data at-rest, such as within an FTPS or SFTP file server.
DLP and SFTPPlus MFT configuration options
For managed file transfer, data in-motion is of priority concern and is within the realm of control for file transfer software. Data at-rest is also another concern, but controls can also be distributed to controls permissioned by the OS file system.
The use of secure file transfer protocols as well as other processes for secure file transfer should form part of the stock for data loss prevention - transmission security. These services and configuration options can be configured using SFTPPlus.
An SFTPPlus feature, Digital signature validation can be configured to check if files have a valid signature:
SIGNED_CONTENT,SIGNATURE
The signature validation process is based on the RSA Digital Signature Algorithm PKCS#1 v2.1 also known as RSASSA-PSS and documented in RFC 3447.
Post process actions may also be added as part of the automated, client transfer rule in order to contain policy rules. A file dispatcher can then be set so that a transfer is quarantined via a separate folder if it has failed a policy rule.
A UUID prefix can also be appended to a file name in order to create unique names so that for each data uploaded, even if duplicate, there is a unique filename.
For authorization control, SFTPPlus administrators can apply permissions to specific groups or users. These permissions will help determine the access to which resources within the file transfer home directory of that user, and other the specific access rights. Permissions can also be set depending on regular expressions (regex), such as disallowing certain file formats. Through the options covered above, administrators can secure data or set permissions to ensure certain resources are not being inappropriately accessed or changed.
For more details about the above configuration options, please consult our documentation or talk to the Support team.
Audit trails for DLP
While operating, SFTPPlus will emit a set of events. Each event has a unique ID and defines a specific operation carried out by the server.
An example of an audit trail upon first connection to an FTP service is below:
| 20076 2018-03-07 19:44:05 ftp-only-1 Process 0.0.0.0:0 Service “ftp” started on “0.0.0.0:10023” using “ftp” protocol. | 10033 2018-03-07 19:44:10 ftp-only-1 Unknown 127.0.0.1:51290 New FTP/FTPS client connection made.
Administrators can gather a comprehensive picture of data-handling activities performed by users through the detailed, server-side audit trail. For example, see below audit trail for an attempt to access an authorized resource:
| 40007 2018-03-28 11:10:25 Process alice 127.0.0.1:52064 HTTP/HTTPS file access successfully started in "/ftps-folders/alice_files" as "/".
Through this online record of server events, organizations can be made aware for the purposes of any legal framework or compliance obligations.
Please see our Users Guides for specific examples pertaining to audit trails for HIPAA/HITECH, and GPG/PMO obligations. More articles are being written for other compliance and regulations.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
Introducing SFTPPlus to high availability and resiliency
Tue 23 January 2018 | article infrastructure
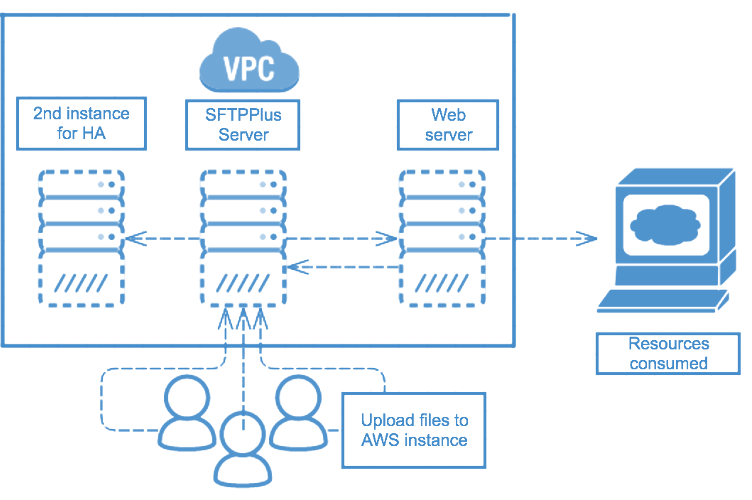
Where does SFTPPlus sit in your IT infrastructure
The SFTPPlus software stands at the OSI Layer 7 or the TCP Layer 4. In order to have a fully fault tolerant system, you need to implement resilience at all the other layers including the OS. SFTPPlus can be integrated with external tools in order to meet the requirements for a fault tolerant infrastructure.
For those not familiar with OSI and TCP please read on.
SFTPPlus on the OSI
The OSI model is a model that characterizes and standardizes communication functions. The layers range from layer 1 right through to layer 7. In the OSI, or Open Systems Interconnection model, SFTPPlus sits in the OSI Layer 7 or on the application layer.
The application layer sits at the top of the OSI model and is the software, hence the name application, layer between the end-user and the networking layers underneath.
In order to have a fault tolerant system, SFTPPlus on the upper layer 7 will need to be integrated with the bottom layers.
SFTPPlus on the TCP
In addition to the OSI model, another way of understanding where SFTPPlus plays a role in your infrastructure is via the TCP layer. SFTPPlus sits in the TCP Layer 4 or the application layer. This is the topmost layer which defines the TCP/IP application protocols and how SFTPPlus interfaces with the Transport layer, the layer below the application layer, and other services that use the network.
Installing SFTPPlus in high availability and resilient environments
The following are introductory information for this topic.
About high availability
High availability means creating a system that is always available for use. It could be a percentage of 99.99% uptime guaranteed. In this case, you will be looking at a downtime of merely five minutes of time over the course of the year.
There are extra items that one can add to ensure that this system is available at the guaranteed uptime rate. In this case, one can look into active-active or active-passive scenarios. To build a system that is highly available means that there may be an additional cost associated with ensuring this.
About resilience
The following can be deduced as a definition of a resilient control system:
"A resilient control system is one that maintains state awareness and an accepted level of operational normalcy in response to disturbances, including threats of an unexpected and malicious nature"
High availability and resilience tend to be used interchangeably. However, having a highly available system does not necessarily mean that all required functions are still in use and available. This is where having a resilient system come into action. Even if a system has high availability, can it still function to a required level of standard, operational normalcy? You will still wish to utilize a system with the same users, storage and database as found in the usual system.
About fault tolerance
On the event of failure, the system remains available in order to maintain the high uptime. There may be a performance break or slow down but the services are still available.
You may add additional devices or protocols for a fault tolerant system - RAID set up, multiple network paths for fault tolerance (on the event of a failed network path) and load balancers are such examples.
About clustering
Clustering involves creating a cluster of two or more nodes or members that work together in order to perform an action. They can be grouped in the following major types; storage, high availability, load balancing and high performance clusters.
The main clusters that relates to SFTPPlus in a given system are high availability and load balancing types of clusters.
High availability clusters involve the provision of highly available services by ensuring that any single points of failure are eliminated. This is done by failing over services from one cluster node to another should that node be no longer in operation. This ensures the ability to maintain data integrity.
Load balancing clusters sends off network requests to a number of cluster nodes in order to balance the request load among the cluster nodes. This ensures scalability of a network since administrators can match the number of nodes according to load requirements through load balancing algorithms.
How can SFTPPlus be integrated in these environments
Active-Active and Active-Passive Scenarios
Active-active and Active-passive are two types of cluster configurations in a high availability scenario.
The details between these two scenarios are laid out below from Sybase.
Active-Passive configurations
Setup: A single Adaptive Server runs either on the primary node or on the secondary node. The Adaptive Server runs on the primary node before a fail over and the secondary node after fail over.
Failover: When a system fails over, the Adaptive Server and its associated resources are relocated to, and restarted on, the secondary node.
Failback: Failback is a planned fail over or relocation of the Adaptive Server and its resources to the primary node. Failback is not required, but can be done for administrative purposes.
Client Connection failover: During failover and failback, clients connect to the same Adaptive Server to resubmit uncommitted transactions. Clients with the failover property reestablish their connections automatically.
How to set up SFTPPlus in active-passive scenarios
In this infrastructure scenario, the second system is offline and only commences when the main SFTPPlus system is down.
Since the server.ini configuration is stored in a single file, you can create a file copy task to keep the system configurations in sync. Make sure to also transfer additional files that are required - such as SSH keys, and SSL keys and certificates - to ensure a smooth transition. When it is time to use the secondary system, the SFTPPlus instance will then read the latest server.ini configuration file.
Active-Active configurations
Setup: Two Adaptive Servers are configured as companion servers, each with independent workloads. These companions run on the primary and secondary nodes, respectively, as individual servers until one fails over.
Failover: When fail over occurs, the secondary companion takes over the devices, client connections, and so on from the primary companion. The secondary companion services the failed-over clients, as well as any new clients, until the primary companion fails back and resumes its activities.
Failback: Failback is a planned event during which the primary companion takes back its devices and client connections from the secondary companion to resume its services.
Client Connection failover: During failover, clients connect to the secondary companion to resubmit their uncommitted transactions. During failback, clients connect to the primary companion to resubmit their transactions. Clients with the failover property reestablish their connections automatically.
How to set up SFTPPlus in active-active scenarios
In this infrastructure scenario, both SFTPPlus systems are receiving and processing requests. If one system goes down, the other will handle all the requests.
To implement SFTPPlus in this scenario, a simple file copy will not work. This is because running SFTPPlus instances will not check changes in the local file configuration (server.ini) in order to reconfigure. In addition, there are other files that are also required - such as all SSH keys in use and other related files, all SSL certificates required, any logs that need to be kept for auditing purposes, any externally referenced scripts used in pre- and post- transfer processing, and so on.
One method of achieving an active/active implementation is to manually set up the 2 nodes to rely on a single external authentication method (HTTP or LDAP). In this way, accounts are managed in the single external system, and those accounts will be automatically available for both SFTPPlus instances.
Installing SFTPPlus for disaster recovery
Disaster recovery is part of business continuity plans (or business continuity and resiliency plans) which is the process of creating systems of prevention and recovery to deal with potential threats to a company. The use of the term “recovery” has also been used when talking about resiliency.
Providing that the server configuration and related configuration files are properly maintained and backed-up, you can integrate SFTPPlus as part of your disaster recovery plans.
Conclusion and next steps
The application of these does not immediately guarantee results in achieving high availability or resiliency. Please consider these guides merely as a layer within multiple others when implementing a high available, resilient and secure managed file transfer solution.
Since features are constantly changed, we did not touch on any specifics within SFTPPlus. Please consult our documentation for the configuration and operations information, as well as practical users guides.
This resource is written as of SFTPPlus version 3.29.0.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.