Articles from security category
- ⬅ All articles
- 🗂 Categories
- 🔖 ftp (1)
- 🔖 infrastructure (3)
- 🔖 privacy (1)
- 🔖 compliance (1)
- 🔖 client-side (1)
- 🔖 general (84)
- 🔖 blog (6)
- 🔖 press (2)
- 🔖 australia (1)
- 🔖 client (17)
- 🔖 release (81)
- 🔖 article (14)
- 🔖 security (24)
- 🔖 server (19)
- 🗄 Archive
- 📌 2012 (1)
- 📌 2013 (1)
- 📌 2014 (2)
- 📌 2016 (2)
- 📌 2017 (2)
- 📌 2018 (15)
- 📌 2019 (1)
Beschränkter Benutzerzugriff auf vertrauenswürdige IP-Adressen für SFTP und FTPS
Thu 15 August 2019 | security blog

Es ist üblich, einen Datenaustausch- Server mithilfe von Firewall-Regeln zu sichern, die nur eingehende Verbindungen von vertrauenswürdigen Partnern zulassen.
Angenommen, Sie haben einen US-amerikanischen Partner namens "ACME AG", der mit dem IP "1.1.1.1", mit dem Benutzer "acme-inc" zu Ihrem Server die Verbindung herstellt und einen weiteren deutschen Partner namens "AlleWerkzeuge AG", der sich vom IP `` 5.5.5.5`` mit dem Benutzer alle-werkzeuge-ag mit Ihrem Server verbindet.
Sie können Ihre Firewall so konfigurieren, dass nur Verbindungen aus einer Liste von vertrauenswürdigen IPs, wie `` 1.1.1.1`` und `` 5.5.5.5``, zugelassen werden. Die Firewall kennt jedoch keine Benutzernamen. So kann das Konto "acme-inc" auch dann eine Verbindung herstellen, wenn die Verbindung von `` 5.5.5.5`` initiiert wurde, einer IP außerhalb des ACME In Netzwerks.
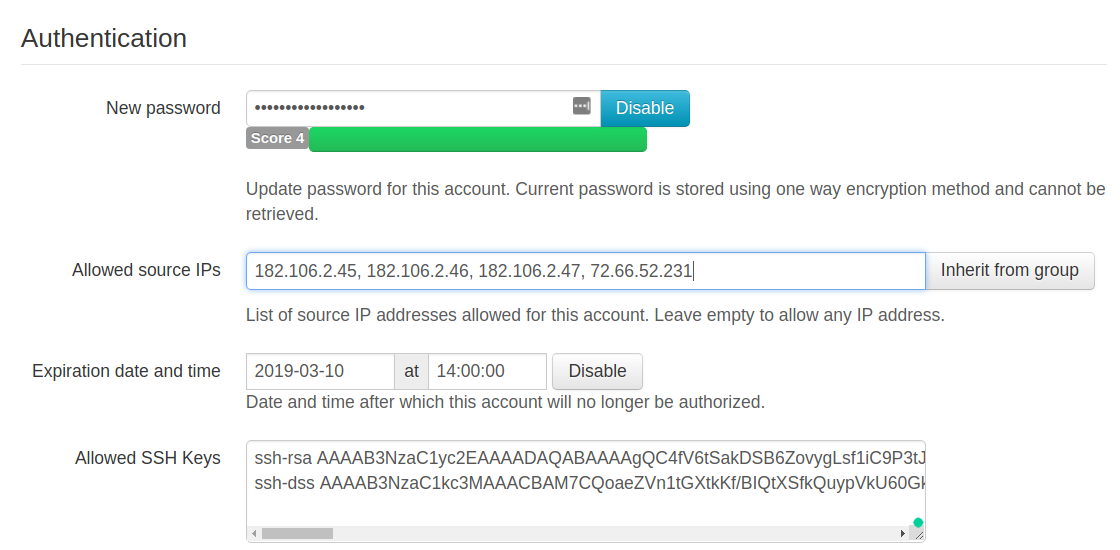
Um die Firewall-Einschränkungen zu ergänzen, können Sie mit SFTPPlus eine feste Liste von vertrauenswürdigen IP-Regeln definieren, mit denen für einen bestimmten Benutzer die Verbindungen zugelassen werden.
Eine solche Konfiguration kann per Benutzer, aber auch per Gruppe definiert werden. mit mehreren Benutzern, die ihre Konfiguration von der Gruppe erben.
Um die Verbindung eines bestimmten Benutzers über SFTP oder FTPS zu dem Dateiübertragung-Server nur auf einem bestimmten IP (oder auf bestimmte IPs) zu beschränken, können Sie in SFTPPlus die Konfigurationsoption `` source_ip_filter`` verwenden.
Der Fernzugriff wird verweigert, wenn der Benutzer sich von einer Quelladresse verbindet, die nicht auf der Whitelist eingetragen ist.
Unten sehen Sie einen Screenshot unserer webbasierten Verwaltungskonsole, die eine solche Konfiguration darstellt.
Weitere Informationen zur Sicherung Ihrer SFTP/FTPS und HTTPS Dienste mit SFTPPlus in unserer documentation page.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.
SFTPPlus Release 3.39.0
Fri 05 October 2018 | release security
We are announcing the latest release of SFTPPlus version 3.39.0.
Customers using the SCP protocol are urged to upgrade to this version. Any previous version contains a security issue when overwriting files over SCP.
New Features
- In the event handler configuration, it is now possible to filter the events based on their groups. [#2483]
- When the remote FTP/FTPS server supports the MLST command, SFTPPlus will use it to determine the existence of remote paths. [client-side][ftp][ftps] [#3885]
- The events emitted at the start or at the end of a client-side file transfer now contain the size of the file, duration and transfer speed. [client-side] [#5067]
Defect Fixes
- When overwriting files using the SCP file transfer, the content of the existing file is completely erased. In previous versions, when overwriting an existing file with a new file which was smaller in size, the resulting file would still have the file size of the previous file, with the extra data kept from the previous file. [security][server-side][scp] [#5087]
- When using execute_on_destination_before in a transfer for which the destination location is stopped, the transfer will automatically start the location. In previous versions, the transfer would failed as the location was stopped, requiring a manual start of the location. [client-side] [#3511]
- When checking the existence of a remote FTP file, the operation now fails when the server returns an error other than 'Path not found'. In previous versions, the error was ignored and the path was considered as non-existing. [client-side][ftp][ftps] [#3576]
- FTP/FTPS client operation can now successfully detect the absence of a file on a remote server. [client-side][ftp][ftps] [#3885]
- You can now disable the timeout for the FTP data connection by setting its value to 0. In previous versions, when set to 0, the connection was disconnected right away due to the timeout. [server-side][ftp][ftps] [#5049]
- When changing the extra_data configuration for the HTTP event handler, the Local Manager UI now shows that a restart is required for the event handler. [#5079]
- You can now change from the Local Manager the list of SSH ciphers available to the SFTP and SCP file transfer services. This was a regression introduced in 3.37.0. [server-side][sftp][scp] [#5085]
Deprecations and Removals
- When a FTP server-side operation fails due to a permission error, the error code is now 553. In previous versions, it was 550, which was the same error code for Path not found or the generic error code for other error cases. [server-side][ftp] [#3576]
You can check the full release notes here.
SFTPPlus Release 3.37.1
Thu 13 September 2018 | security release
We are pleased to announce the latest release of SFTPPlus version 3.37.1.
Defect Fixes
- The HTTP API authentication for an account now fails when the account is accepted by the remote HTTP API but the associated group is disabled. [server-side][security] [#5058]
- A defect was fixed in Local Manager which was causing the Local Manager to fail on Internet Explorer 11. [#5061]
Deprecations and Removals
- Event with ID 20060 was removed and replaced by event with ID 20136. [server-side] [#5058]
You can check the full release notes here.
SFTPPlus Release 3.35.0
Tue 03 July 2018 | security release
We are pleased to announce the latest release of SFTPPlus version 3.35.0.
New Features
- The OpenSSL library used by SFTPPlus on Windows was updated to OpenSSL 1.1.0h. [#4579]
- It is now possible to define virtual folders that are available to all accounts from a group. These virtual folders can point to directories outside an account's locked home folder. [server-side] [#4928]
- It is now possible to allow authentication of operating-system accounts only for those belonging to a configured group. [server-side] [#4962]
- Python version on all supported platforms except HP-UX was updated to 2.7.15. Consequently, the Expat libraries bundled with Python were updated to 2.2.4 on these platforms. [#4579]
Defect Fixes
- An internal error is no longer raised when a SSH client sends a message for a method which is not supported by the SSH transport. Instead, the client receives a standard SSH not-implemented error. [server-side][sftp] [#4579]
- The speed of the SSH handshake for the SFTP service has been improved. Previously, there was a noticeable difference for certain customers during the SSH handshake authentication process. [server-side][sftp][#4579]
- pyOpenSSL was updated on AIX and Solaris to fix CVE-2013-4314. The X509Extension in pyOpenSSL before 0.13.1 does not properly handle a '0' character in a domain name in the Subject Alternative Name field of an X.509 certificate, which allows man-in-the-middle attackers to spoof arbitrary SSL servers via a crafted cert issued by a legitimate Certification Authority. The experimental packages for HP-UX are still vulnerable to this and will to be fixed in a future release.[server-side][#4579]
- Once set, passwords for locations or email resources are no longer readable from Local Manager. A password can be read only before being set and applied. Afterwards, its value cannot be read, only updated. [security] [#4938]
- Comma-separated configuration values may now contain comma characters, as long as they are enclosed in double quotation marks. [#4951]
- The event generated when a peer's certificate validation fails during a TLS/SSL handshake now shows the detailed error message, not just the error code. [#4979]
You can check the full release notes here.
Setting up security scanners for your SFTPPlus MFT Server
Wed 20 June 2018 | article security
Introduction
The following is a short guide on how you can set up a security scanner for your SFTPPlus MFT Server installation. For this guide, we have chosen a free and open source scanner, OWASP Zed Attack Proxy or zaproxy, as an example.
Of course, there are a number of other software and tools that you can use and all with varying mileage.
We can also cover these other tools, depending on interest. Therefore, if you would like to see more of these types of posts from SFTPPlus, please make sure to contact us. If you are not familiar with the terms, or need to do some background reading, you can scroll down to the Other resources section first.
To be kept up to date with the latest developments, please sign up to our security advisories.
About OWASP Zed Attack Proxy or zaproxy
For our server-side scan of the SFTPPlus MFT service (HTTPS and HTTP) and Local Manager, we used the OWASP Zed Attack Proxy or zaproxy which is a free and open source penetration testing tool released by OWASP and developed for website application security testing.
After running the application, you can generate a report for further consumption. The report contains OWASP ZAP specific terminology. These are listed below for your reference.
WASC ID This is the ID provisioned by the Web Application Security Consortium (WASC) Threat Classification project. Read more about WASC here.
CWE ID This is the ID provisioned by the Common Weakness Enumeration (CWE) project. Read more about CWE here.
Confidence This is the description of how confident the result is in the validity of the finding.
- False Positive - for potential issues that one will later find is actually not exploitable.
- Low - for unconfirmed issues.
- Medium - for issues that zaproxy is somewhat confident in.
- High - for findings that zaproxy is highly confident in.
- Confirmed - for confirmed issues.
Risk Description of how serious the risk is. The risk shown is from the report generated by zaproxy.
Source This is the ZAP policies code. Read more here.
Using zaproxy to conduct an active scan on SFTPPlus services
Prerequisite
As a standard prerequisite, you will need the zaproxy application, a version of SFTPPlus Server software and consent to conduct these types of scanning activities if you are doing so on behalf of a group or organization.
For this example, we will be conducting an active scan of the SFTPPlus HTTP service available on the default port 10080. There are also other web-browser based services that you can scan such as the SFTPPlus Local Manager on port 10020 and the HTTPS service available on the default port 10443.
In addition, scanning can affect availability. We recommend a backup of your database.
What is an active scan?
Active scanning will attempt to find potential vulnerabilities by using known attacks against the selected target, in this case the SFTPPlus HTTP service. It should be noted that active scanning can only find certain types of vulnerabilities. Logical vulnerabilities, such as broken access control, will not be found by any active or automated vulnerability scanning. Manual penetration testing should always be performed in addition to active scanning to find all types of vulnerabilities.
Also, scanning will unearth results that also need to be consumed and understood by the relevant parties.
Setting up an active scan
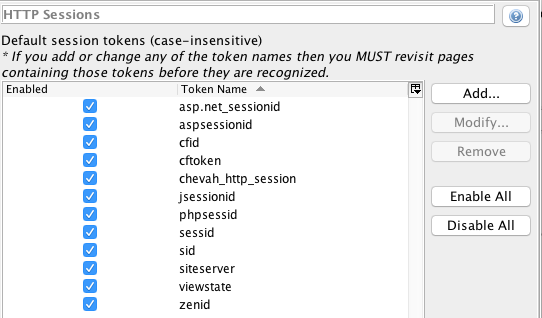
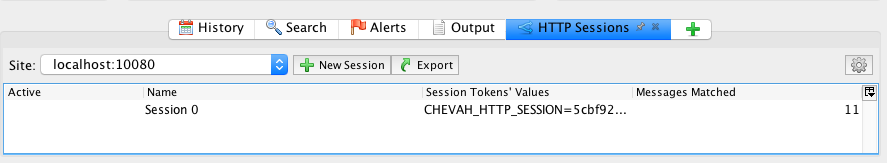
In order to attack the authenticated part of the HTTP service, we will need to add the HTTP session token in the zaproxy application.
Go to 'Tools' -> 'Options' -> 'HTTP Sessions' -> add chevah_http_session in the Token Name. Make sure that this token is enabled then select 'OK'.
See screenshot below:
Make sure that the 'HTTP Sessions' tab is open. To view the 'HTTP Sessions' tab, go to 'View' -> select 'Show Tab' -> then 'HTTP Sessions'. At this stage, the pane is empty but it will soon be populated with the correct values in the later steps.
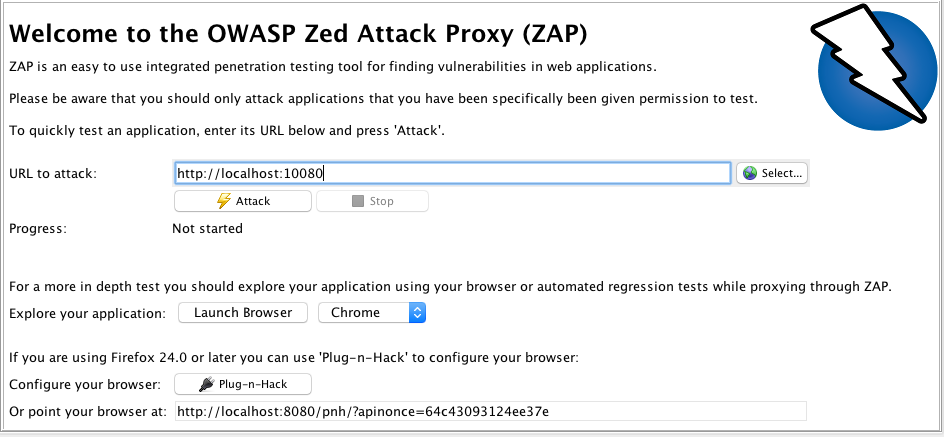
In the 'Quick Start' pane, add http://localhost:10080 in the 'URL to attack' field. This is the URL for the SFTPPlus HTTP web-browser based file manager service. Do not press 'Attack', instead scroll down and select 'Launch Browser' for Chrome.
See screenshot below:
The reason why you cannot go straight to attacking/scanning the resource is because it still requires authentication. If not authenticated with zaproxy, you will see an error Failed to attack the URL: received a 401 response code.
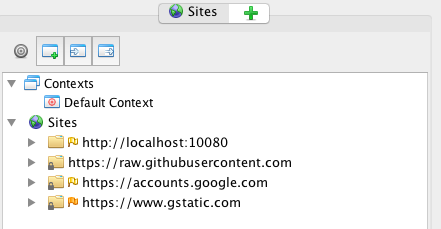
After selecting 'Launch Browser', a new Chrome browser will launch and you will start seeing activity in the 'Sites' pane. The browser should have 'Explore your application with ZAP' as the landing page.
Open the URL http://localhost:10080 in the Chrome browser and login to the test file transfer account.
Once logged in, you should now see http://localhost:10080 in the 'Sites' pane.
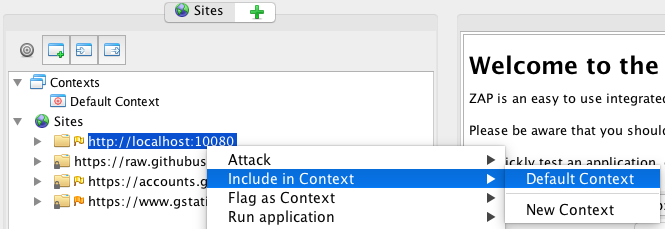
In the 'Sites' pane, right-click over the http://localhost:10080 URL and select 'Include in Context' then 'Default Context'.
In the 'HTTP Sessions' pane, you should now see that there is a new session added for the site localhost:10080 with values populated in the 'Session Tokens' Values' field.
If you do not see any values, launch the SFTPPlus HTTP service again and log in.
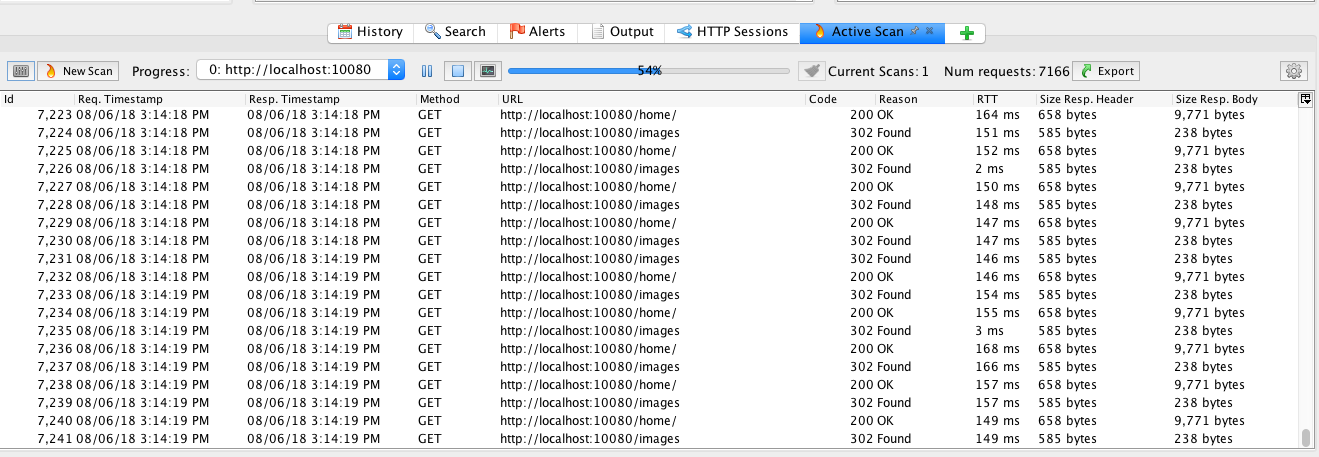
Back in the 'Sites' pane, right click over the localhost URL, select 'Attack' -> 'Active Scan'.
For one of our tests, we only wanted to scan the HTTP headers to see if the version of SFTPPlus would be able to escape possible CSRF attacks. In this case, for the 'Input Vectors' tab, only the 'HTTP Headers, All Requests' vector was selected. You can choose other vectors according to your own requirements or you can opt to choose all vectors.
Allow the scan to work. The times can vary.
Alerts are located in the 'Alerts' tab. You can read what the Alert is about from this pane. Please note that alerts may include alerts from associated third party services.
You can generate the report after the scan has completed.
Select 'Report' on the top menu > 'Generate HTML Report' and save the file.
Other reporting file formats can be used such as JSON, XML, Markdown.
Example scan result
Below is an example scan of what you may find. Please note that results will differ depending on factors such as your installation, configuration and SFTPPlus version:
Low Risk: Web Browser XSS Protection Not Enabled Details: URL: Risk: Low Confidence: Medium CWE ID: 933 - Security Misconfiguration - https://cwe.mitre.org/data/definitions/933.html WASC ID: 14 - Server Misconfiguration http://projects.webappsec.org/w/page/13246959/Server%20Misconfiguration Source: Passive (10016 - Web Browser XSS Protection Not Enabled) Description: Web Browser XSS Protection is not enabled, or is disabled by the configuration of the 'X-XSS-Protection' HTTP response header on the web server Other info: The X-XSS-Protection HTTP response header allows the web server to enable or disable the web browser's XSS protection mechanism. The following values would attempt to enable it: X-XSS-Protection: 1; mode=block X-XSS-Protection: 1; report=http://www.example.com/xss The following values would disable it: X-XSS-Protection: 0 The X-XSS-Protection HTTP response header is currently supported on Internet Explorer, Chrome and Safari (WebKit). Note that this alert is only raised if the response body could potentially contain an XSS payload (with a text-based content type, with a non-zero length). Solution: Ensure that the web browser's XSS filter is enabled, by setting the X-XSS-Protection HTTP response header to '1'. Reference: https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet https://blog.veracode.com/2014/03/guidelines-for-setting-security-headers/
Upon seeing reports in regards to XSS vulnerabilities, we have fixed user input escaping where error messages where done without the user input and also added validation of the user input.
Therefore, the HTML rendering code for the HTTP service has been added to ensure that this is not the case to secure user input.
As part of this change, we have also added new automated tests for the HTTP service as part of our quality assurance reviews.
Example SFTPPlus audit log during a scan
As you can see, the scan generated some potential CSRF attacks which SFTPPlus version 3.34.1 detected and therefore disconnected against:
| 40018 2018-06-07 11:05:43 Process Unknown 127.0.0.1:58871 Forcing client disconnection at "/unwanted.js" after receiving 0 bytes in body. Response: 400 Possible CSRF
The above is just an example of what you may see in the audit log and is not related to the scan result in the previous section.
The reason why you are seeing this in the audit trail is that we now enforce requests from the same origin including basic requests such as GET and even older HTTP requests such as POST.
This is to ensure that requests from the outside boundary (the Internet) are not interacting with the safe confines of the HTTP file service or the Local Manager.
We have ensured that the browser is forced to download data, rather than execute data, after checking the Origin and Referrer headers are of the same source.
What to do if you find an issue
The first step is to check if you have the latest version of SFTPPlus. New versions will contain not only new features, but also defect fixes including security bug fixes.
The second step is to look at the type of alert and to do a manual confirmation of the feasibility of the alert (for example, if it's a false positive) and to confirm the results from zaproxy. The alerts are meant to be guidance for further investigations.
If there is a bug found, please do not hesitate to contact SFTPPlus Support with your defect report.
Keep up to date by signing up to our security advisories
SFTPPlus continues to be focused on automated, non-interactive file transfers in a secure fashion. Our security practices have been designed to make this a reality for our clients.
To be kept up to date with the latest security advisory and news, please subscribe to out newsletter here.
Other resources
The details in this resource is for guidance only. Influences such as own security policies, requirements, and threat models should be considered when adopting this type of guidance.
This resource is written as of SFTPPlus version 3.34.1.
SFTPPlus MFT bewerten
Die in diesem Artikel aufgeführten Funktionen sind nur einige ausgewählte Funktionen aus vielen heute verfügbaren Integrations- und Konfigurationsoptionen. Sprechen Sie mit dem Support-Team über Ihre Anforderungen an die Datenaustausch-Software.
SFTPPlus MFT Server unterstützt FTP, Explizites FTPS, Implizites FTPS, SFTP, SCP, HTTP und HTTPS.
SFTPPlus MFT ist als On-Premise-Lösung erhältlich, die auf Windows, Linux und macOS unterstützt wird.
Es ist auch in der Cloud als Docker-Container, AWS- oder Azure-Instanzen und viele andere Cloud-Anbieter verfügbar.
Fordern Sie mit dem unten stehenden Formular eine Testversion an.