Security Advisory on CSRF and XSS attacks affecting HTTP/HTTPS services
- ⬅ All articles
- 🗂 Categories
- 🔖 ftp (1)
- 🔖 infrastructure (3)
- 🔖 privacy (1)
- 🔖 compliance (1)
- 🔖 client-side (1)
- 🔖 general (84)
- 🔖 blog (6)
- 🔖 press (2)
- 🔖 australia (1)
- 🔖 client (17)
- 🔖 release (81)
- 🔖 article (14)
- 🔖 security (24)
- 🔖 server (19)
- 🗄 Archive
- 📌 2001 (3)
- 📌 2005 (1)
- 📌 2006 (1)
- 📌 2007 (1)
- 📌 2008 (1)
- 📌 2012 (1)
- 📌 2013 (3)
- 📌 2014 (13)
- 📌 2015 (20)
- 📌 2016 (23)
- 📌 2017 (14)
- 📌 2018 (38)
- 📌 2019 (17)
Tue 24 April 2018 | security
Customers using HTTP/HTTPS services should upgrade to 3.33.0
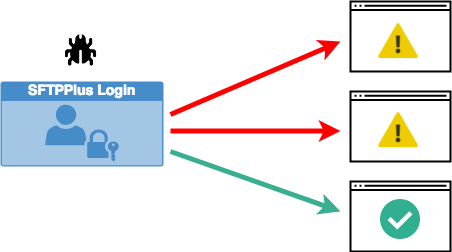
The SFTPPlus version 3.33.0 release is a major security update for the HTTP/HTTPS file transfer service and the SFTPPlus Local Manager service.
This update addresses the vulnerabilities concerning Cross-Site Request Forgery Attacks and Cross-Site Scripting Attacks on the aforementioned services.
Customers that are not accessing SFTPPlus services from a web browser are not exposed to these vulnerabilities.
In addition, customers utilizing FTP, FTPS, SFTP, and SCP protocols are not affected.
We recommend that all affected customers should upgrade to the SFTPPlus 3.33.0 release, since it includes fixes for Cross-Site Request Forgery and Cross-Site Scripting vulnerabilities.
To mitigate the risk in older SFTPPlus versions, we recommend the following actions:
- Do not have other tabs or windows open in the same browser while being authenticated to a SFTPPlus service, or
- Use a private window or a separate profile / container.
- Log out from the SFTPPlus service as soon as your have completed your tasks.
The aforementioned security issues were due to ProAtria not performing a security audit of SFTPPlus, when used from an interactive browser.
Taking into consideration the current challenges of HTTP security, we have now updated our security practices and implemented automated tests. These tests will cover the HTTP-specific attacks against SFTPPlus when accessed from a web browser.
SFTPPlus continues to be focused on automated, non-interactive file transfers in a secure fashion. Our security practices have been designed to make this a reality for our clients.
You can check the rest of the 3.33.0 release notes here.